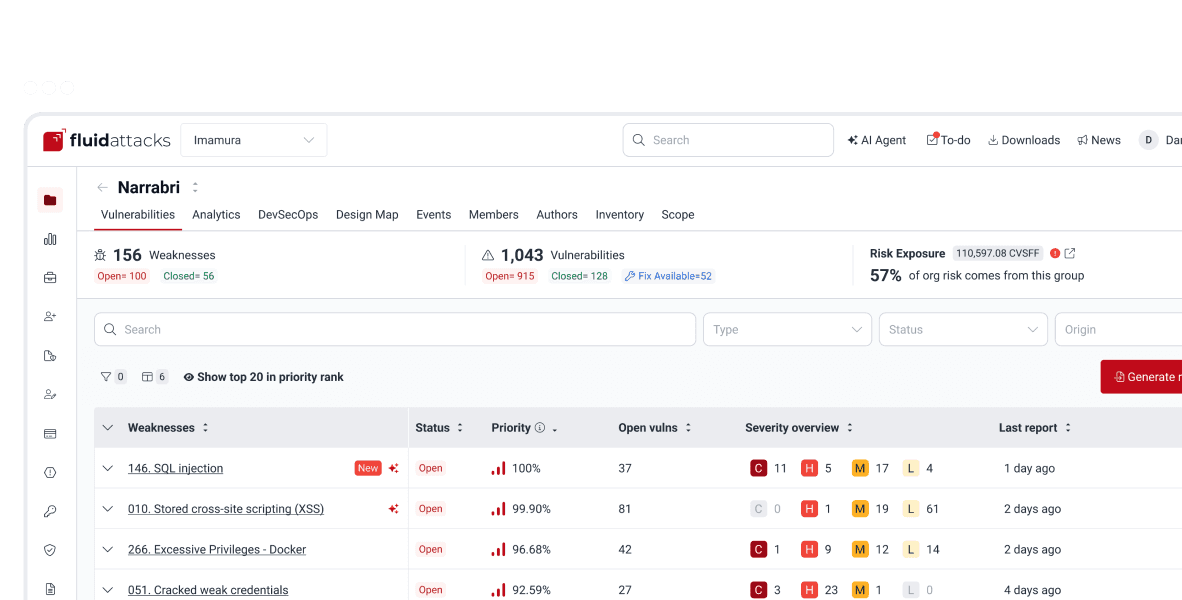
Application security posture management (ASPM)
Get correlated, prioritized and ready-to-fix security findings
The evolution of application security orchestration and correlation (ASOC)
Contextualization, prioritization and management of security risks
All findings from our tools and pentesters on a single platform



Companies already benefiting from Fluid Attacks' application security posture management solution
Why you should choose Fluid Attacks' ASPM solution
Why you should choose Fluid Attacks' ASPM solution

AST keeping pace with application development
Our ASPM solution offers you continuous application security testing (AST) and reporting from the start and throughout your SDLC to prevent bottlenecks when changes are going into production, reduce remediation costs and help avoid security incidents.
Consolidation and analysis of results in one place
Appropriate risk scoring and prioritization
Management and tracking of standards compliance

AST keeping pace with application development
Our ASPM solution offers you continuous application security testing (AST) and reporting from the start and throughout your SDLC to prevent bottlenecks when changes are going into production, reduce remediation costs and help avoid security incidents.
Consolidation and analysis of results in one place
Appropriate risk scoring and prioritization
Management and tracking of standards compliance

AST keeping pace with application development
Our ASPM solution offers you continuous application security testing (AST) and reporting from the start and throughout your SDLC to prevent bottlenecks when changes are going into production, reduce remediation costs and help avoid security incidents.
Consolidation and analysis of results in one place
Appropriate risk scoring and prioritization
Management and tracking of standards compliance

AST keeping pace with application development
Our ASPM solution offers you continuous application security testing (AST) and reporting from the start and throughout your SDLC to prevent bottlenecks when changes are going into production, reduce remediation costs and help avoid security incidents.
Consolidation and analysis of results in one place
Appropriate risk scoring and prioritization
Management and tracking of standards compliance

Fluid Attacks is not just an application security posture management solution
Discover our Continuous Hacking and understand why it is key to developing secure software without affecting your DevOps speed.

All-in-one testing approach
We combine multiple testing techniques in a single solution (SAST, AI SAST, SCA, DAST, SCR, PTaaS and RE).

Generative AI-assisted remediation
We use generative artificial intelligence to provide you with custom fix options for specific vulnerabilities in your code.

Continuous expert support
Our pentesters can help your development and security teams solve questions about the most complex vulnerabilities.

Security across your SDLC
Our reattacks check your remediation success, and we break the build in your CI/CD pipelines to avoid unsafe deployments.

Fluid Attacks is not just an application security posture management solution
Discover our Continuous Hacking and understand why it is key to developing secure software without affecting your DevOps speed.

All-in-one testing approach
We combine multiple testing techniques in a single solution (SAST, AI SAST, SCA, DAST, SCR, PTaaS and RE).

Generative AI-assisted remediation
We use generative artificial intelligence to provide you with custom fix options for specific vulnerabilities in your code.

Continuous expert support
Our pentesters can help your development and security teams solve questions about the most complex vulnerabilities.

Security across your SDLC
Our reattacks check your remediation success, and we break the build in your CI/CD pipelines to avoid unsafe deployments.
Fluid Attacks is not just an application security posture management solution
Discover our Continuous Hacking and understand why it is key to developing secure software without affecting your DevOps speed.

All-in-one testing approach
We combine multiple testing techniques in a single solution (SAST, AI SAST, SCA, DAST, SCR, PTaaS and RE).

Generative AI-assisted remediation
We use generative artificial intelligence to provide you with custom fix options for specific vulnerabilities in your code.

Continuous expert support
Our pentesters can help your development and security teams solve questions about the most complex vulnerabilities.

Security across your SDLC
Our reattacks check your remediation success, and we break the build in your CI/CD pipelines to avoid unsafe deployments.

Fluid Attacks is not just an application security posture management solution
Discover our Continuous Hacking and understand why it is key to developing secure software without affecting your DevOps speed.

All-in-one testing approach
We combine multiple testing techniques in a single solution (SAST, AI SAST, SCA, DAST, SCR, PTaaS and RE).

Generative AI-assisted remediation
We use generative artificial intelligence to provide you with custom fix options for specific vulnerabilities in your code.

Continuous expert support
Our pentesters can help your development and security teams solve questions about the most complex vulnerabilities.

Security across your SDLC
Our reattacks check your remediation success, and we break the build in your CI/CD pipelines to avoid unsafe deployments.
Frequently asked questions
What is application security posture management?
What is application security posture management?
What is application security posture management?
What is application security posture management?
Is ASPM the same as ASOC?
Is ASPM the same as ASOC?
Is ASPM the same as ASOC?
Is ASPM the same as ASOC?
Why is ASPM important?
Why is ASPM important?
Why is ASPM important?
Why is ASPM important?
Do you want to learn more about application security posture management?
Read some of our posts related to this solution.
ASPM is a crucial piece of Fluid Attacks' solution
We offer an all-in-one solution that combines our AI, automated tools and pentesters to help you improve your cybersecurity posture continuously.

Fluid Attacks' solutions enable organizations to identify, prioritize, and remediate vulnerabilities in their software throughout the SDLC. Supported by AI, automated tools, and pentesters, Fluid Attacks accelerates companies' risk exposure mitigation and strengthens their cybersecurity posture.
Targets
Subscribe to our newsletter
Stay updated on our upcoming events and latest blog posts, advisories and other engaging resources.
© 2026 Fluid Attacks. We hack your software.

Fluid Attacks' solutions enable organizations to identify, prioritize, and remediate vulnerabilities in their software throughout the SDLC. Supported by AI, automated tools, and pentesters, Fluid Attacks accelerates companies' risk exposure mitigation and strengthens their cybersecurity posture.
Targets
Subscribe to our newsletter
Stay updated on our upcoming events and latest blog posts, advisories and other engaging resources.
© 2026 Fluid Attacks. We hack your software.

Fluid Attacks' solutions enable organizations to identify, prioritize, and remediate vulnerabilities in their software throughout the SDLC. Supported by AI, automated tools, and pentesters, Fluid Attacks accelerates companies' risk exposure mitigation and strengthens their cybersecurity posture.
Targets
Subscribe to our newsletter
Stay updated on our upcoming events and latest blog posts, advisories and other engaging resources.
© 2026 Fluid Attacks. We hack your software.

Fluid Attacks' solutions enable organizations to identify, prioritize, and remediate vulnerabilities in their software throughout the SDLC. Supported by AI, automated tools, and pentesters, Fluid Attacks accelerates companies' risk exposure mitigation and strengthens their cybersecurity posture.
Targets
Subscribe to our newsletter
Stay updated on our upcoming events and latest blog posts, advisories and other engaging resources.
© 2026 Fluid Attacks. We hack your software.