Stay in ongoing control of your company's risk exposure
Your Dev and Sec teams can rely on a platform that helps them recognize, prioritize, verify, and fix security vulnerabilities detected in your applications.
Companies already benefiting from Fluid Attacks' platform
Everything your teams need to secure your SDLC
Our single pane of glass is at your teams' fingertips throughout the entire software development lifecycle.
IDENTIFICATION
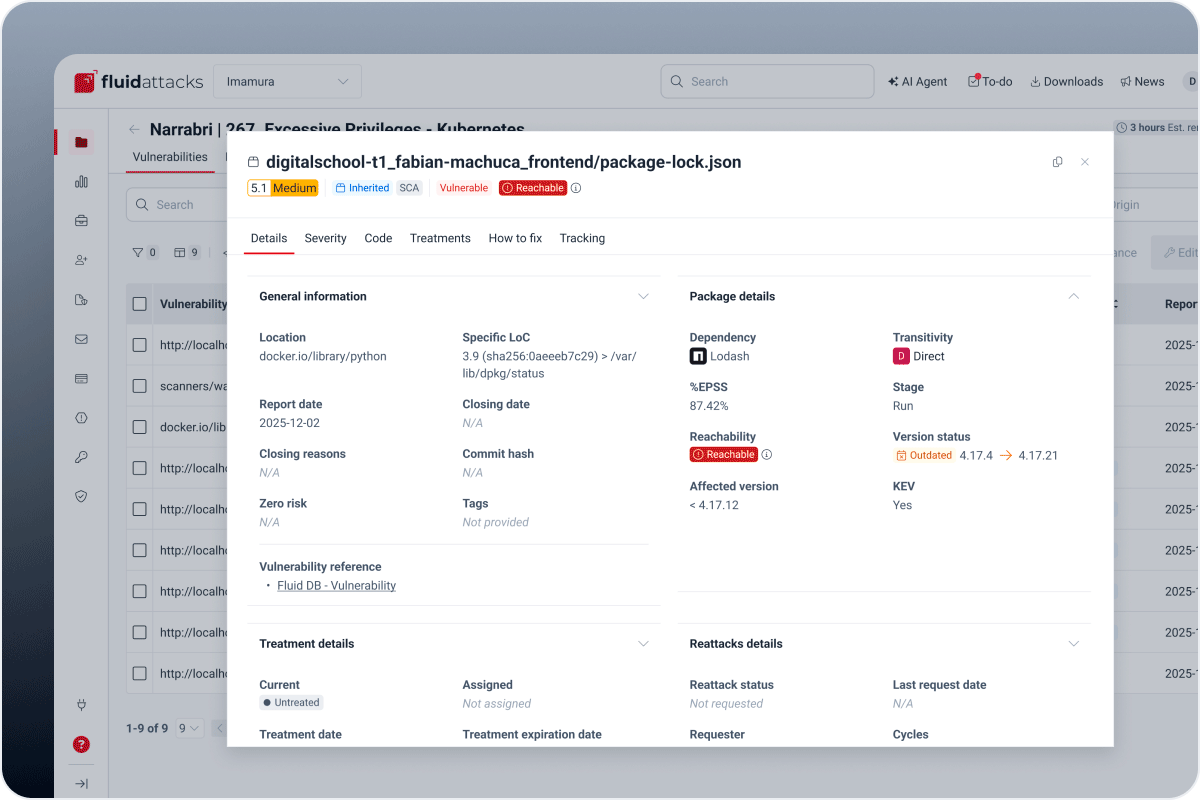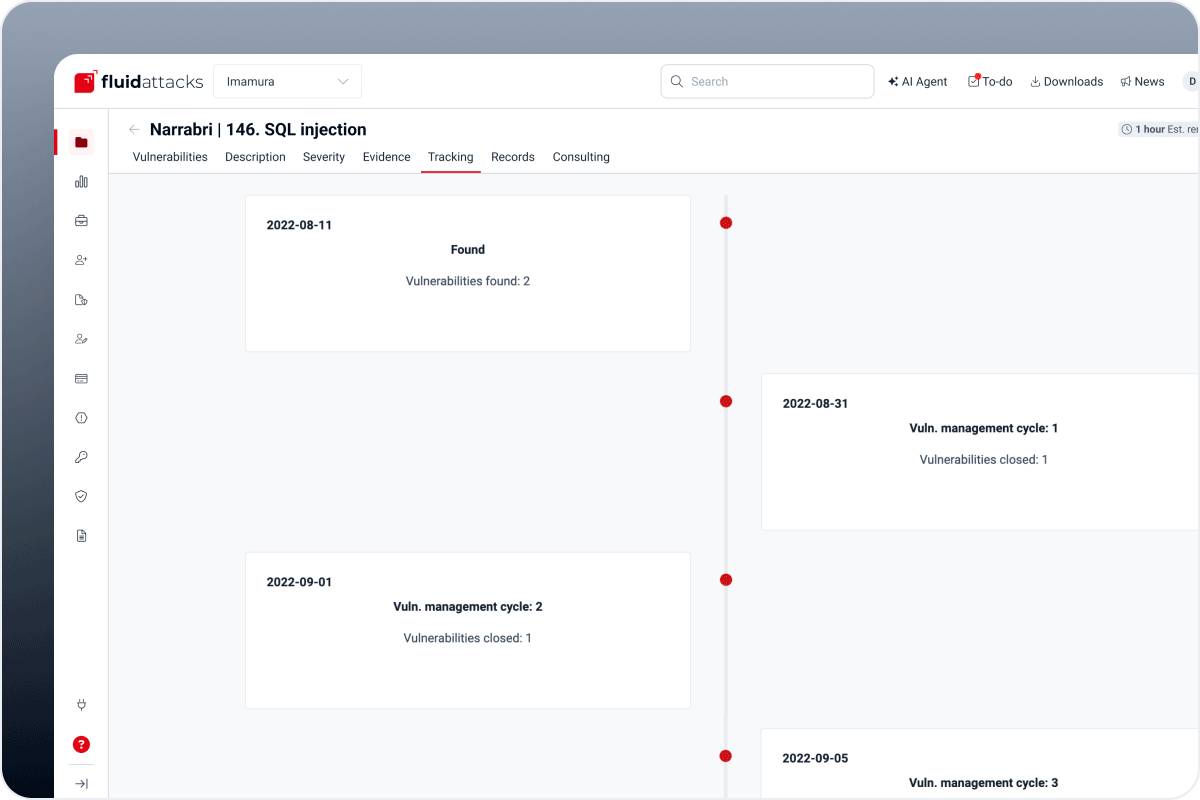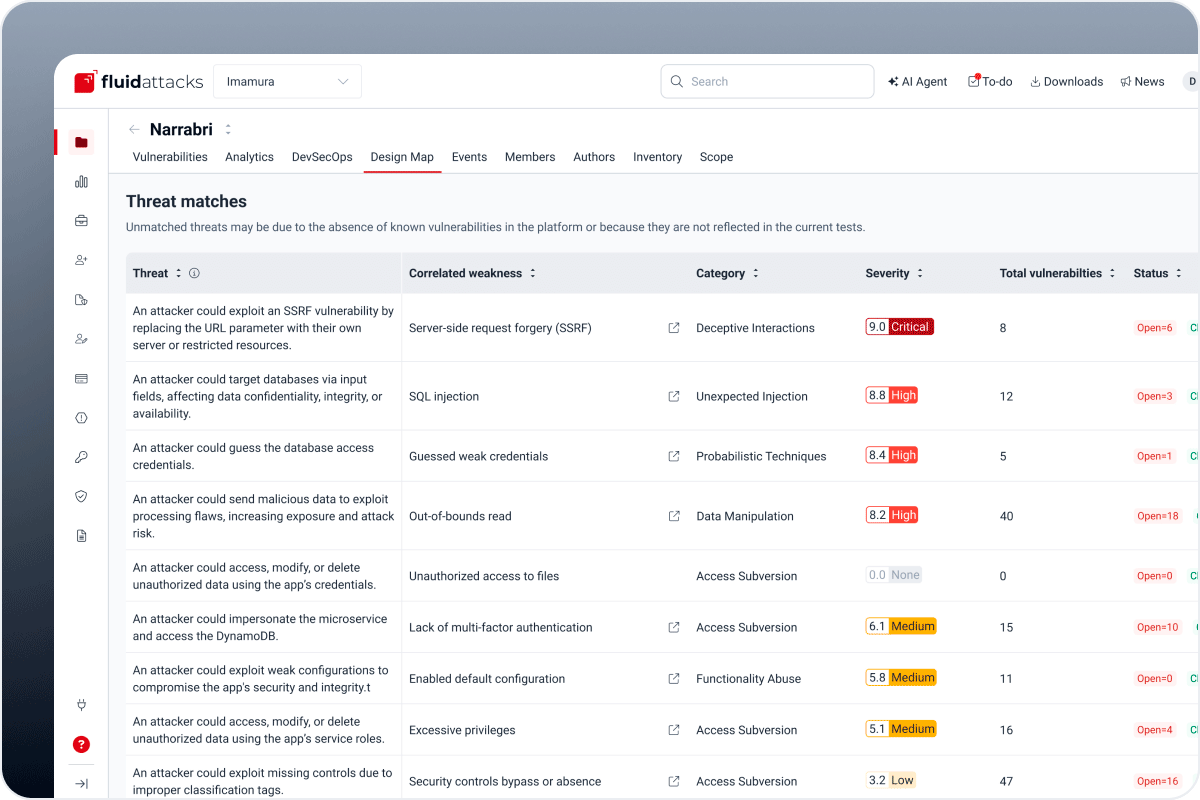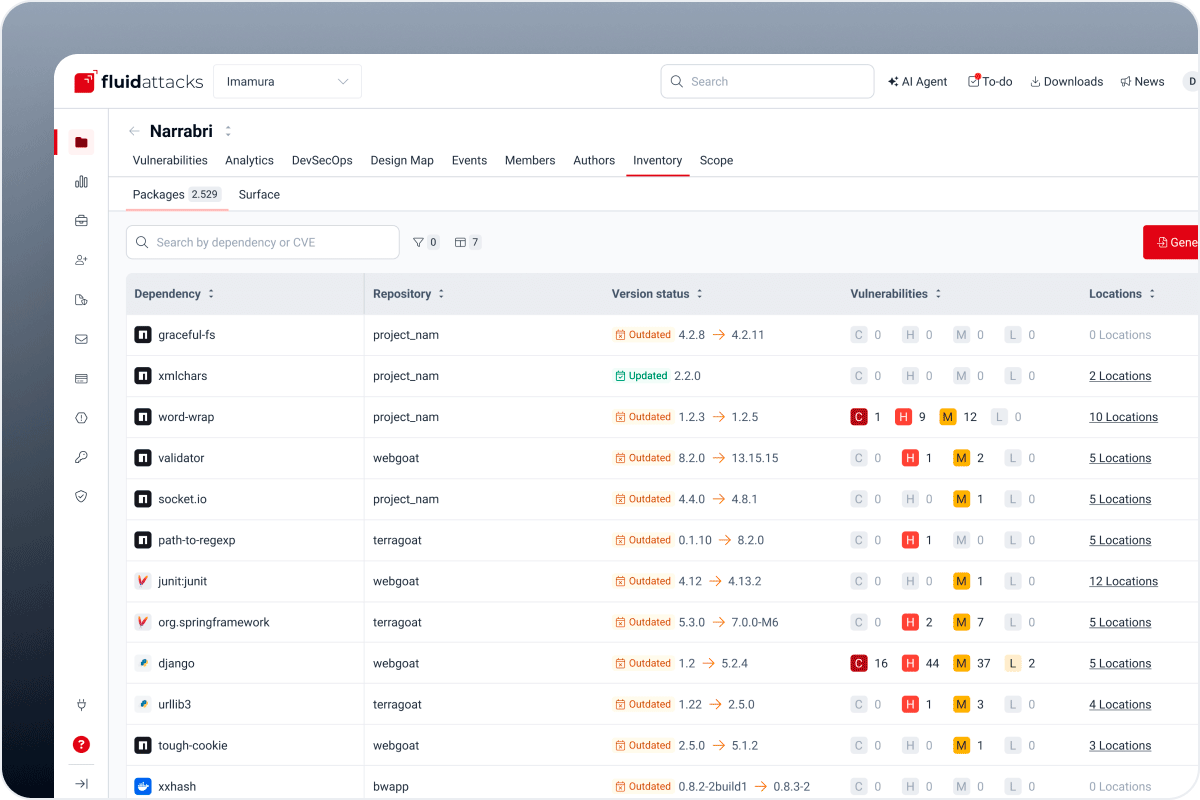
A single source of truth
Centralize every finding from automated scans and manual tests.
Unified view of SAST, AI SAST, DAST, SCA, SCR, RE, and PTaaS results
Insight into both injected and inherited vulnerabilities
Design Map: Upload your security design and automatically correlate it with reported vulnerabilities
Full visibility into vulnerability locations, severities, and priority scores
SBOM view of third-party components that may pose security risks
Track progress across projects, teams involved, and repositories under evaluation
PRIORITIZATION
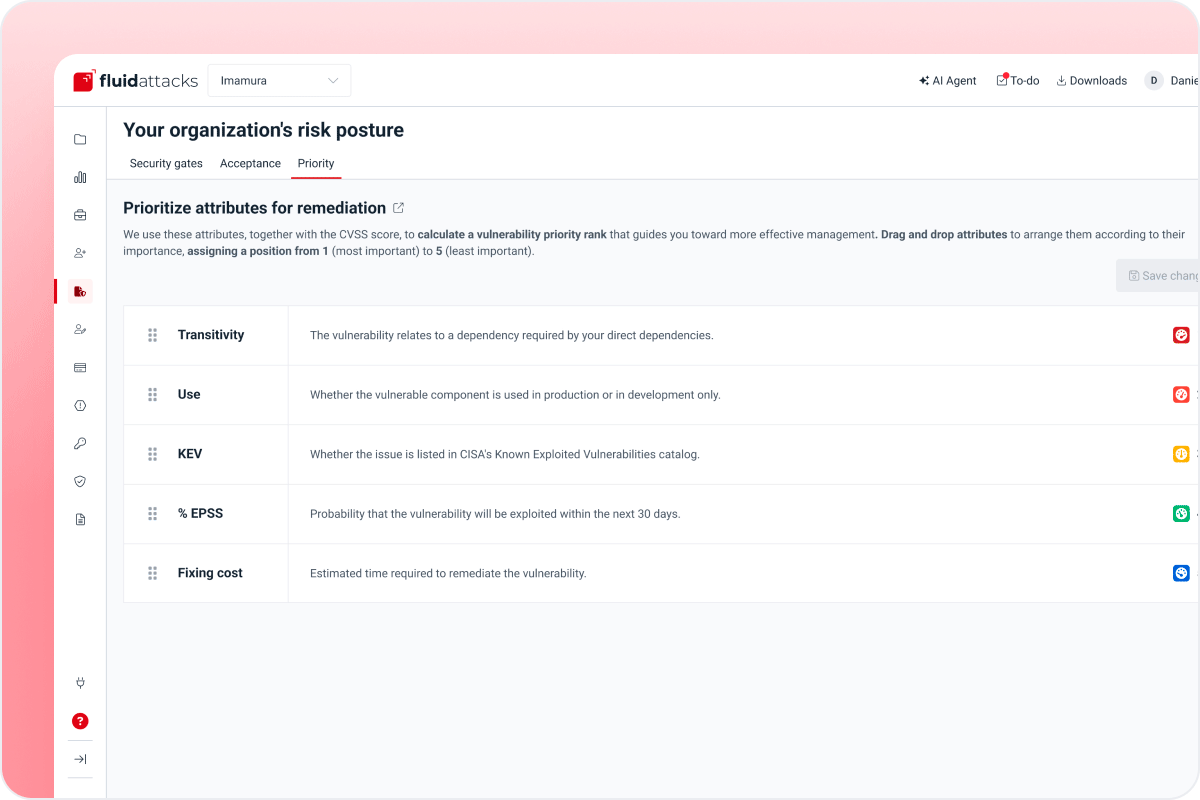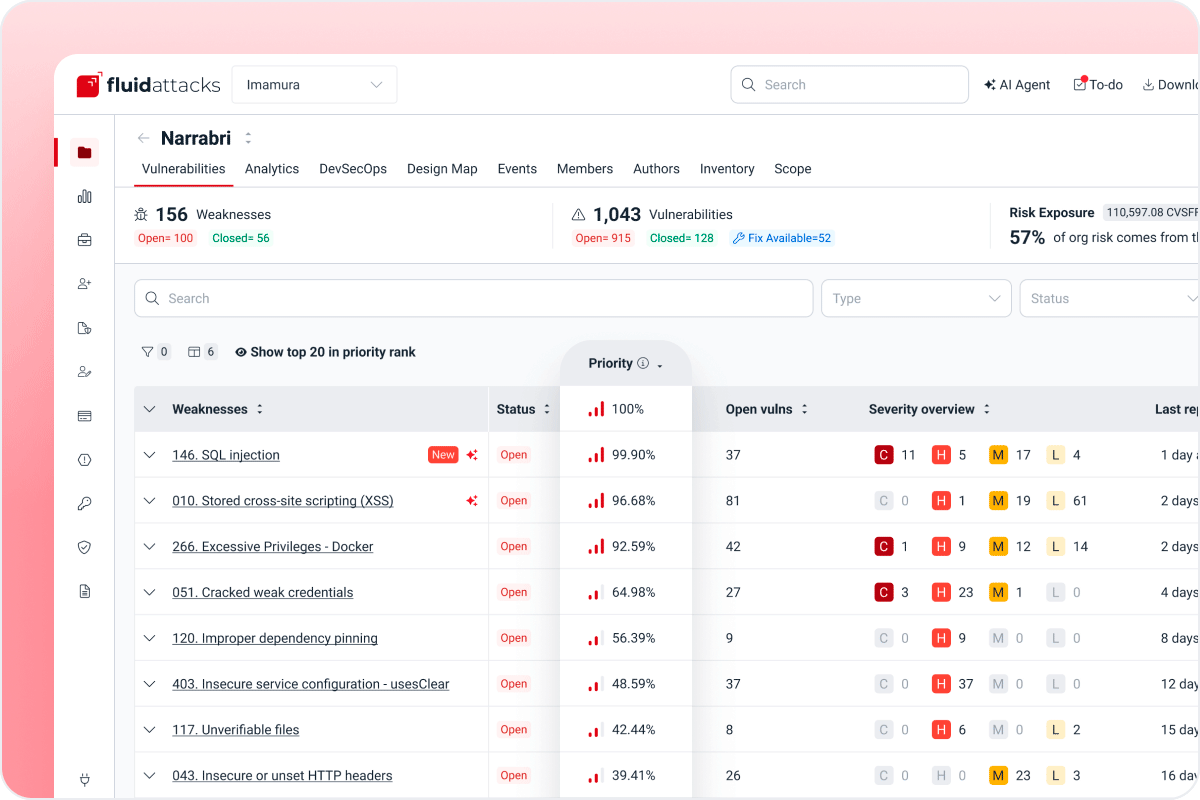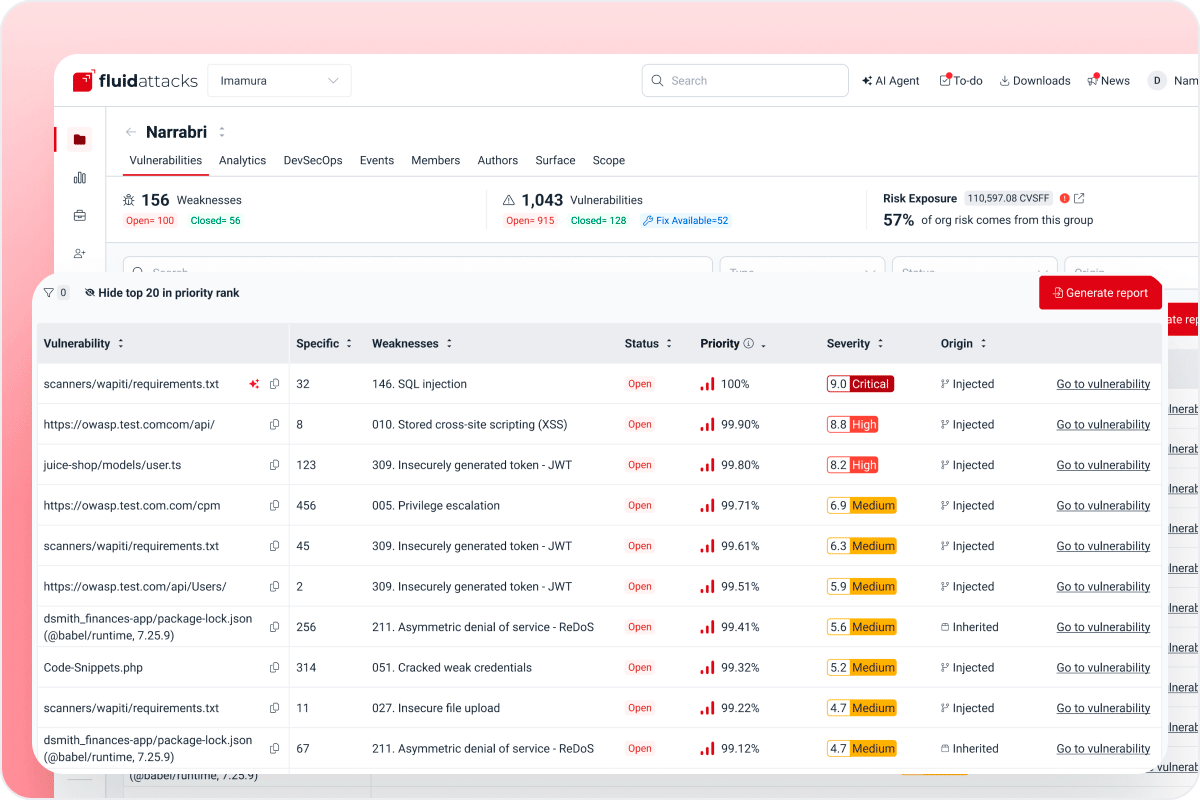
Risk-based prioritization
Focus on what really matters with dynamic, customizable risk scoring.
Priority score based on CVSS and enriched with info on use, reachability, transitivity, KEV, EPSS and fixing cost
Define your policies:
Temporary risk acceptance
Build-breaking thresholds (by CVSS or time)
Permanent acceptance for low-risk vulnerabilities
Auto-removal of inactive users
Criteria weighting for vulnerability prioritization

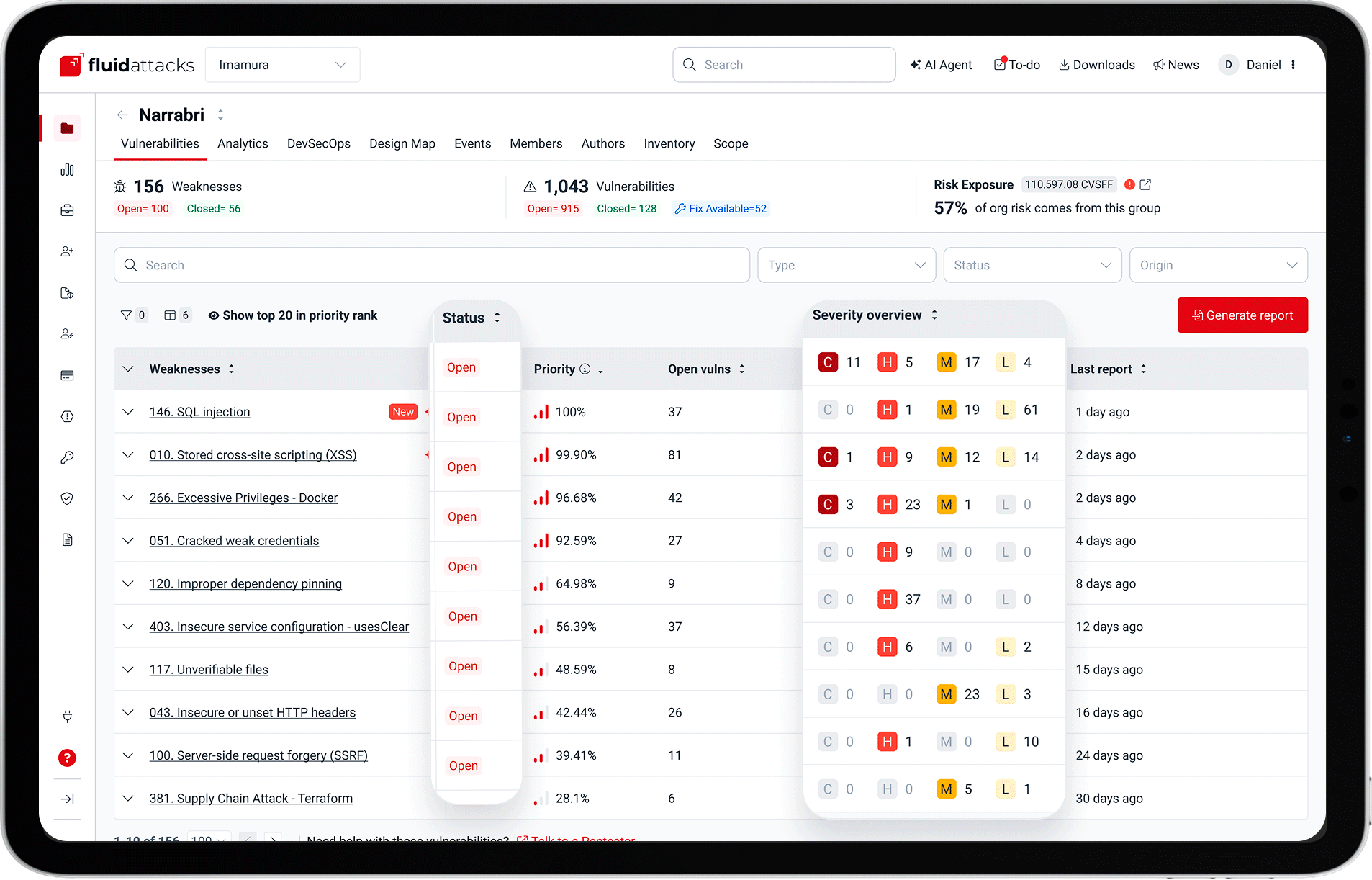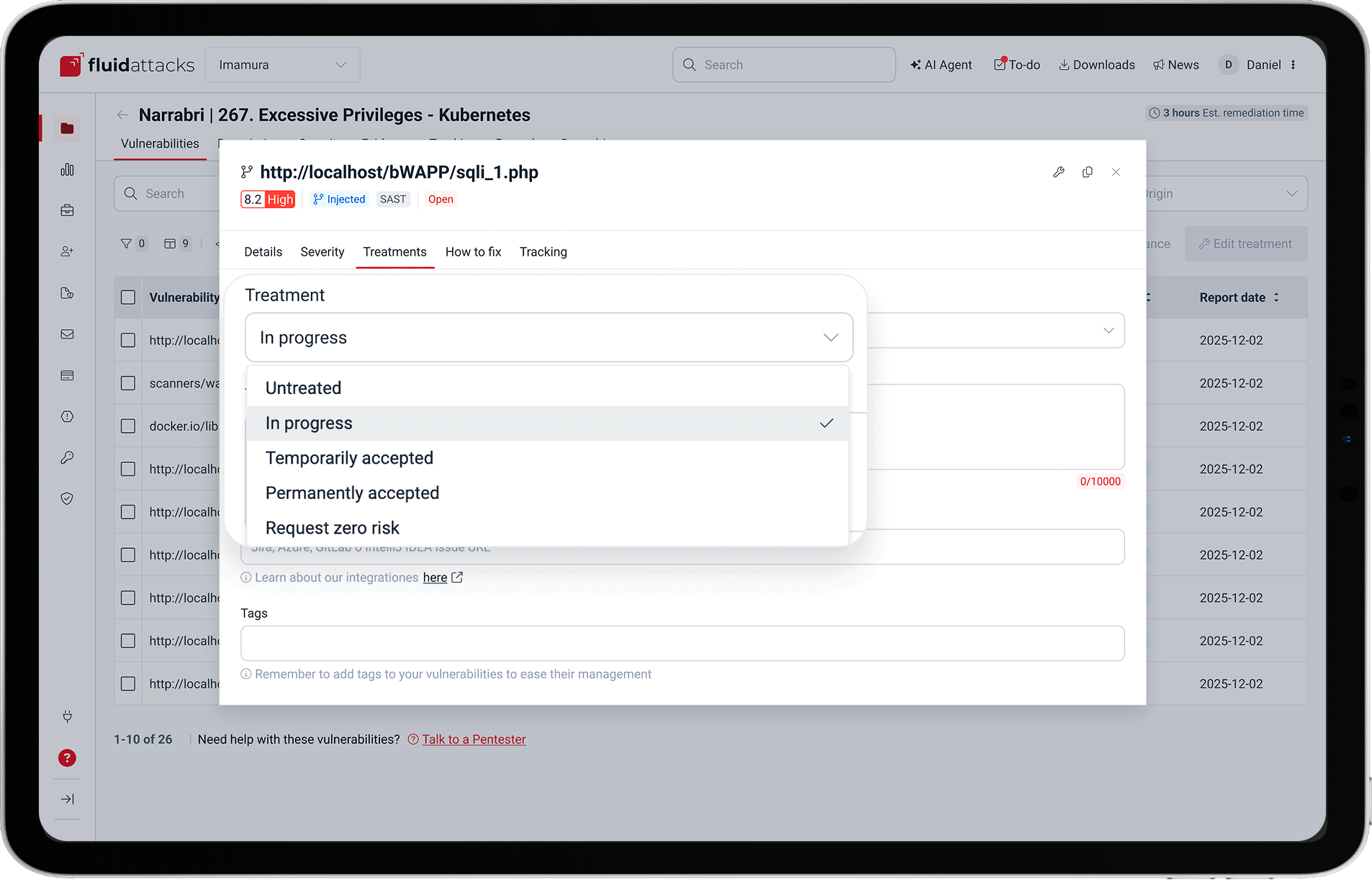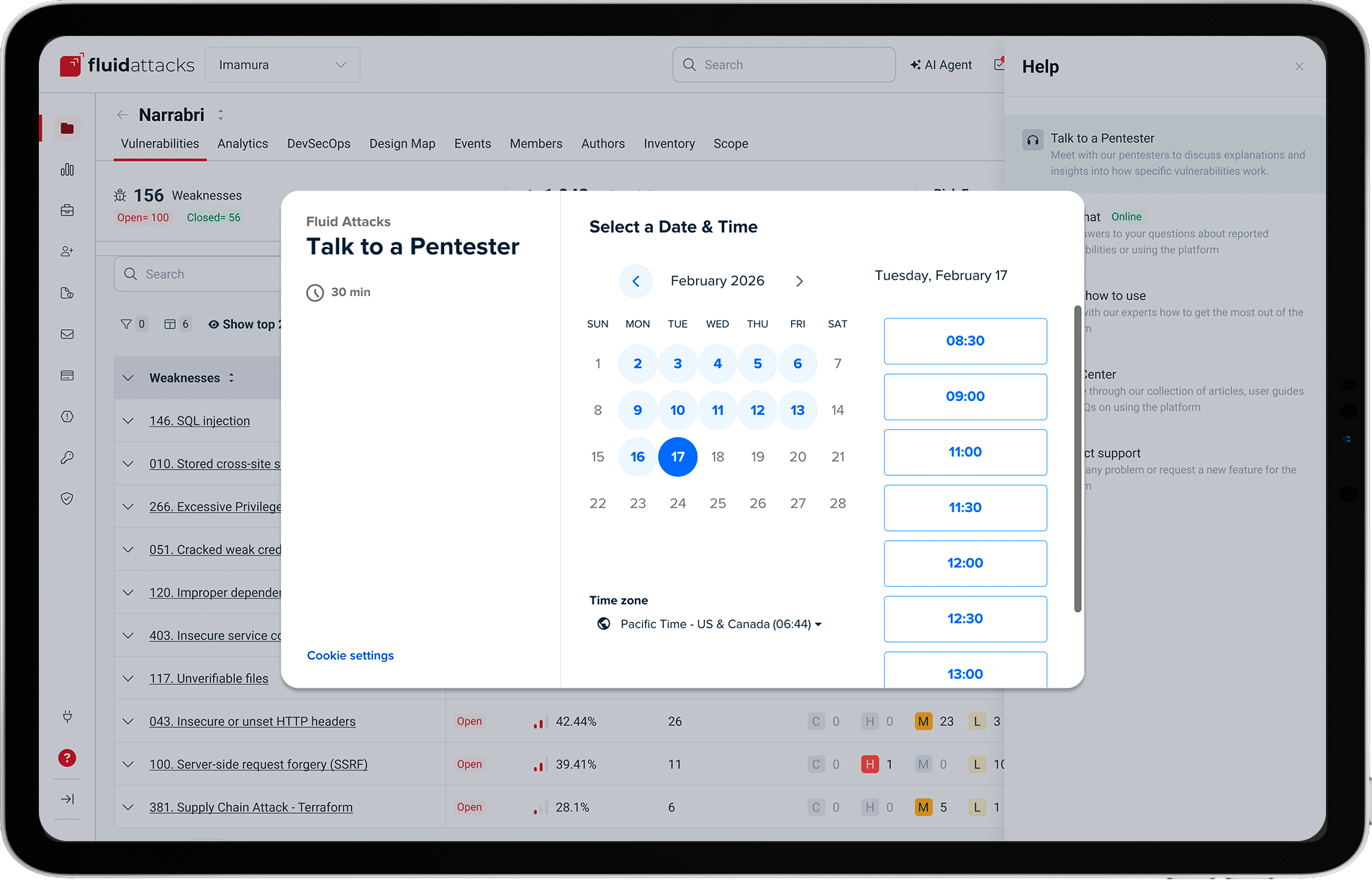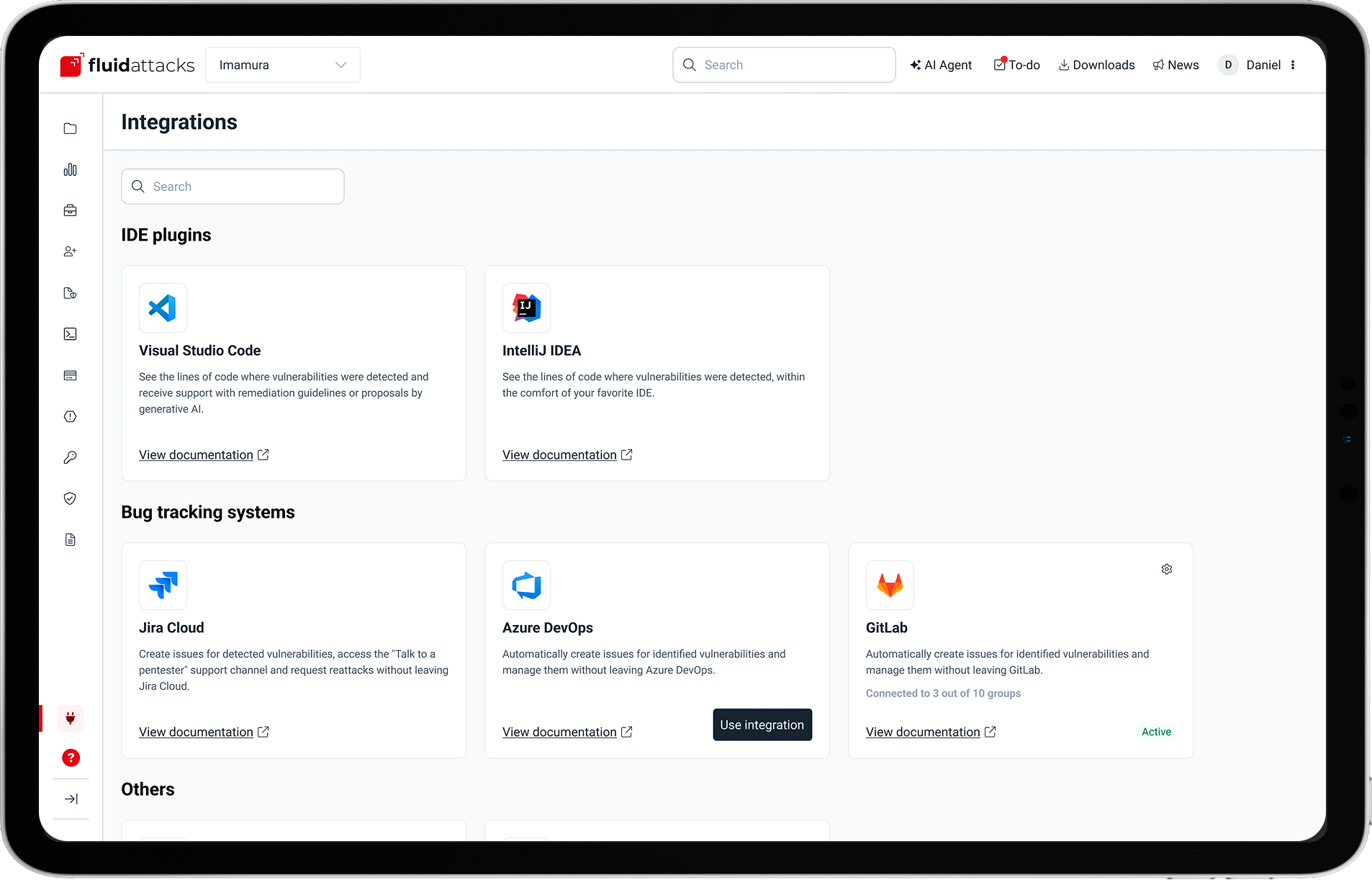
FIXING AND VERIFICATION
Orchestrated remediation
TRACKING
Metrics and reporting
Turn insights into action and prove your security ROI to stakeholders.
MTTR and remediation rates by project
Trend analysis and benchmarks against other orgs
Insights by severity, group, and weaknesses
Compliance-ready reporting (ISO/IEC 27001, SOC 2, NIST, and 64 more)


UNIFIED WORKFLOW
Seamless collaboration
Integrations that engage your team
Connect your IDEs, bug-tracking systems, and CI/CD tools with Fluid Attacks' platform to keep developers in their flow and catch vulnerabilities earlier — no context switching required.
Our ASPM is a core part of our Continuous Hacking solution
We offer an all-in-one solution that combines our platform, AppSec tools, AI, and our team of pentesters to help you continuously improve your cybersecurity posture.