AI security
Adopt AI models
securely
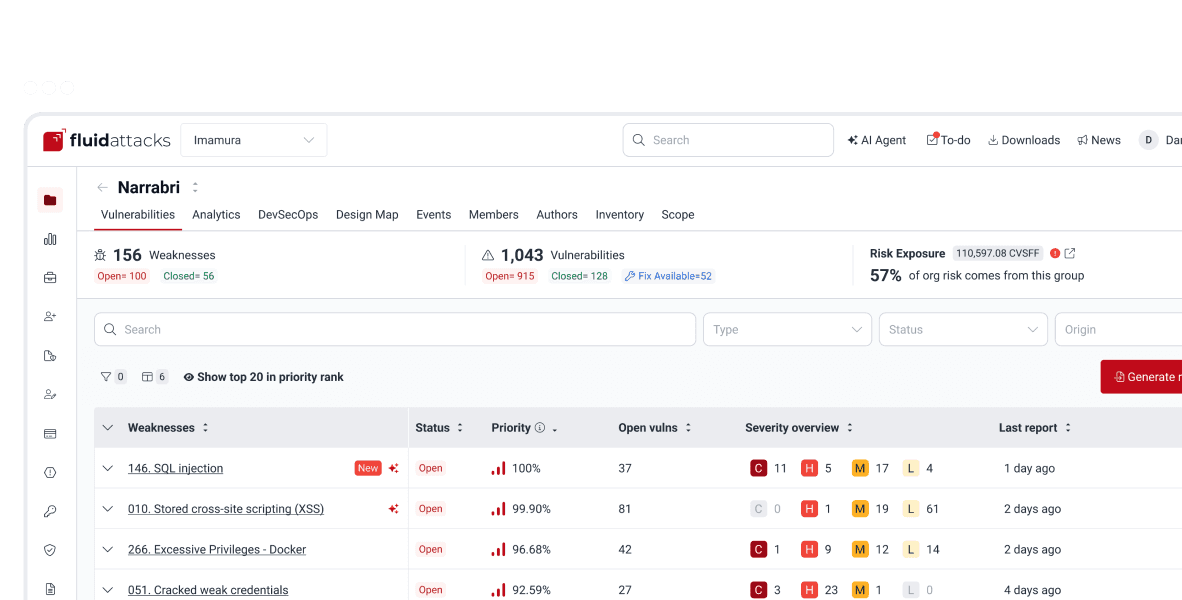
Continuous visibility of risks in AI models, training data and AI services
Specialized vulnerability reporting for GenAI or LLM-based applications
Centralized management and extensive support for vulnerability remediation

Companies already benefiting from Fluid Attacks' AI security solution
Frequently asked questions
What is AI security?
Why is AI security important?
What are the risks of AI?
How does AI security work?
Do you want to learn more about AI security?
Read some of our posts related to this solution.
AI security is a crucial piece of Fluid Attacks' solution
We offer an all-in-one solution that combines our AI, automated tools and pentesters to help you improve your cybersecurity posture continuously.