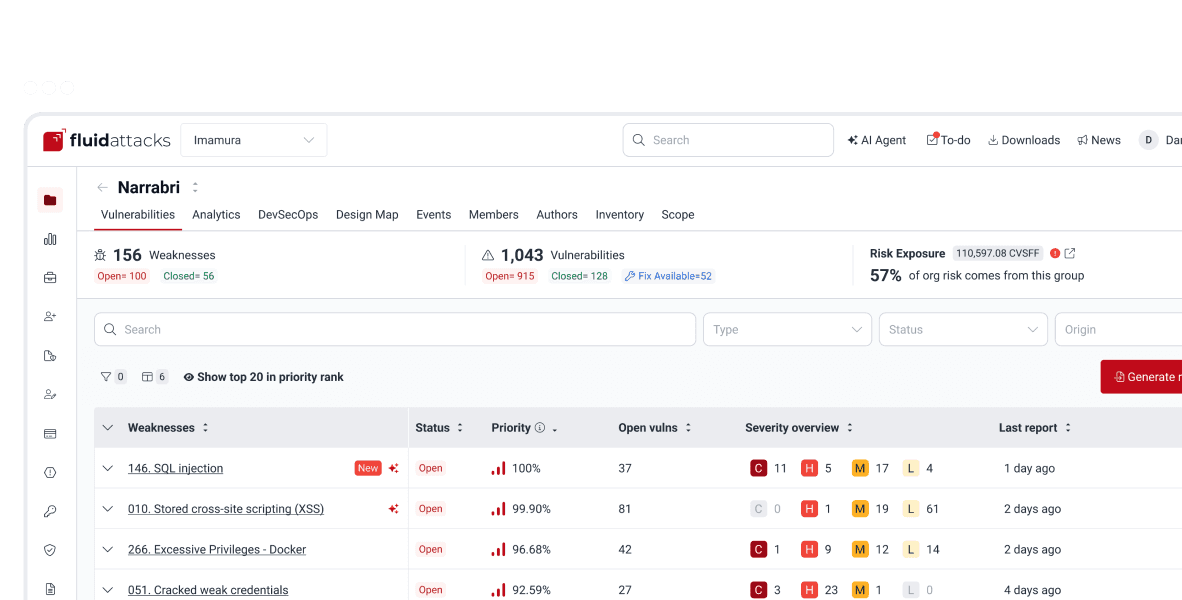
Application security (AppSec)
Secure your apps across the entire SDLC
Security as an essential component in your DevOps approach (DevSecOps)
Multiple testing techniques supporting your software development
Identification and mitigation of risk exposure in your web or mobile apps

Companies already benefiting from Fluid Attacks' AppSec solution
Frequently asked questions
AppSec
What are application security solutions, and why do organizations need them?
What types of security testing are included in application security solutions?
Can application security solutions be integrated into the software development lifecycle (SDLC)?
How frequently should organizations conduct application security assessments?
DevSecOps
What does DevSecOps stand for?
What is DevSecOps methodology?
Why is DevSecOps important?
What are the advantages of DevSecOps vs. DevOps?
How to implement DevSecOps?
What are DevSecOps best practices?
How are application security testing tools used in DevSecOps?
Security testing
How to perform security testing?
What are the types of security testing?
Why is security testing important?
Do automated tools hack?
How do false positives impact software development?
How do false negatives impact software development?
Penetration testing as a service (PTaaS)
What is penetration testing?
What is the primary purpose of penetration testing?
What is the end result of a penetration test?
What is manual pentesting?
What is penetration testing as a service?
How does PTaaS work?
Secure code review
What is secure code review?
How to do a secure code review?
Which secure code review tools are commonly used?
What security requirements do you check when doing secure code review?
Why is secure code review important?
Do you want to learn more about application security?
Read some of our posts related to this solution.
AppSec is a crucial piece of Fluid Attacks' solution
We offer an all-in-one solution that combines our AI, automated tools and pentesters to help you improve your cybersecurity posture continuously.