OpenSearch 3.2.0 - Nested Boolean/Disjunction Asymmetric DoS
8.3
High
Discovered by

Offensive Team, Fluid Attacks
Summary
Full name
OpenSearch 3.2.0 - Nested Boolean/Disjunction Asymmetric DoS via query_string
Code name
State
Public
Release date
Nov 25, 2025
Affected product
OpenSearch
Vendor
OpenSearch
Affected version(s)
>= 3.0.0, < 3.3.0 and < 2.19.4
Fixed version(s)
3.3.0. and 2.19.4
Vulnerability name
Asymmetric denial of service
Vulnerability type
Remotely exploitable
Yes
CVSS v4.0 vector string
CVSS:4.0/AV:N/AC:L/AT:N/PR:L/UI:N/VC:N/VI:N/VA:H/SC:N/SI:N/SA:H
CVSS v4.0 base score
8.3
Exploit available
No
CVE ID(s)
Description
A vulnerability in OpenSearch allows attackers to cause Denial of Service (DoS) by submitting complex query_string inputs that generate deeply nested boolean and non-boolean disjunction query trees. While OpenSearch enforces indices.query.bool.max_clause_count as a per-BooleanQuery node limit, there is no global cap on the total number of query nodes, nor on the fan-out within non-Boolean containers, such as DisjunctionMaxQuery. Attackers can craft inputs to keep each node under the per-node limit while exploding the overall tree size, consuming excessive CPU and memory.
Vulnerability
The core issue is that clause limits are enforced per BooleanQuery node rather than across the entire query tree. The query_string parser and related builders can compose nested groups and disjunctions that avoid per-node limits but dramatically expand the total number of nodes.
Key code paths:
Global limit configuration:
org.opensearch.search.SearchService.INDICES_MAX_CLAUSE_COUNT_SETTING and IndexSearcher.setMaxClauseCount(...) apply a per-node clause cap.
Field expansion limit (not total clauses):
org.opensearch.index.search.QueryParserHelper.checkForTooManyFields(...), called from QueryStringQueryParser.extractMultiFields(...).
Query building (delegation without global cap):
org.opensearch.index.search.QueryStringQueryParser.getBooleanQuery(...) delegates to superclass; relies on Lucene per-node limit.
Enforcement inside MatchQuery (used by MultiMatchQuery):
org.opensearch.index.search.MatchQuery throws IndexSearcher.TooManyClauses on certain graph/phrase paths (per-node).
Non-boolean disjunction growth:
org.opensearch.index.search.MultiMatchQuery and QueryStringQueryParser frequently build DisjunctionMaxQuery aggregates, which are not bounded by the boolean clause limit.
Result: Queries can be constructed where no single BooleanQuery exceeds the clause cap, yet the total query becomes extremely large, leading to CPU and heap exhaustion.
PoC
Patterns that grow query trees while keeping per-node clauses small. In practice, generate programmatically to very large sizes.
Evidence of Exploitation
This vulnerability can be exploited whenever untrusted clients can submit `query_string` queries. Crafted inputs with deeply nested groups and multi-field disjunctions will trigger heavy query construction, rewrite, and scoring, leading to CPU saturation and elevated heap usage.
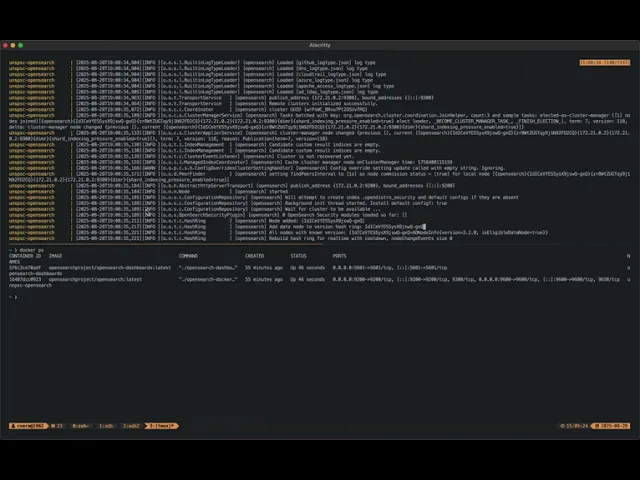
Query String being executed

OpenSearch exited with code 137

Video of exploitation
Our security policy
We have reserved the ID CVE-2025-9624 to refer to this issue from now on.
System Information
OpenSearch
Version 3.2.0
Operating System: Any
References
Github Repository: https://github.com/opensearch-project/OpenSearch
Fixed versions (3.3.0): https://github.com/opensearch-project/OpenSearch/releases/tag/3.3.0
Fixed versions (2.19.4): https://github.com/opensearch-project/OpenSearch/releases/tag/2.19.4
Blog: https://caverav.cl/posts/opensearch-dos/opensearch-dos/
Github Pull: https://github.com/opensearch-project/OpenSearch/pull/19491
Mitigation
An updated version of OpenSearch is available at the vendor page.
Credits
The vulnerability was discovered by Camilo Vera from Fluid Attacks' Offensive Team.
Timeline
Aug 10, 2025
Vulnerability discovered
Sep 4, 2025
Vendor contacted
Sep 4, 2025
Vendor replied
Sep 17, 2025
Follow-up with vendor
Sep 17, 2025
Vendor confirmed
Nov 25, 2025
Vulnerability patched
Nov 25, 2025
Public disclosure
Does your application use this vulnerable software?
During our free trial, our tools assess your application, identify vulnerabilities, and provide recommendations for their remediation.







