Frappe CRM 1.53.1 — Multiple SQL Injections in Dashboard Controller
7.1
High
Discovered by

Offensive Team, Fluid Attacks
Summary
Full name
Frappe CRM 1.53.1 — Multiple SQL Injections in Dashboard Controller
Code name
State
Public
Release date
Nov 26, 2025
Affected product
Frappe CRM
Vendor
Frappe
Affected version(s)
1.53.1
Fixed version(s)
1.54.0
Vulnerability name
SQL Injection
Vulnerability type
Remotely exploitable
Yes
CVSS v4.0 vector string
CVSS:4.0/AV:N/AC:L/AT:N/PR:L/UI:N/VC:H/VI:N/VA:N/SC:N/SI:N/SA:N
CVSS v4.0 base score
7.1
Exploit available
Yes
CVE ID(s)
Description
Multiple endpoints in Frappe CRM 1.53.1 are vulnerable to SQL injection due to unsafe concatenation of the user-controlled user parameter into dynamic SQL statements.
Vulnerability
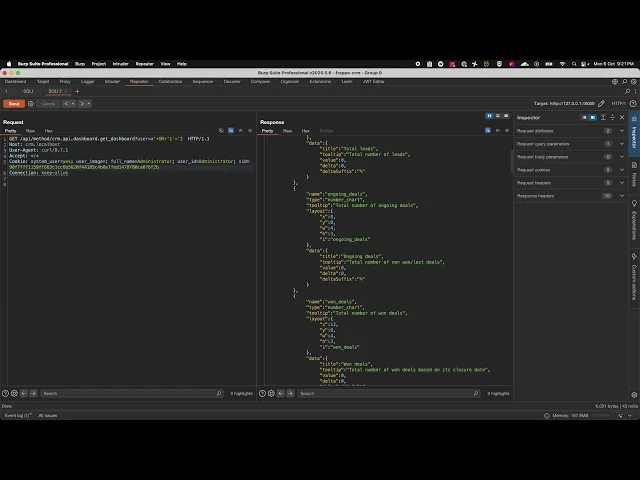
Across crm/api/dashboard.py many helper functions construct SQL queries using a conds string that directly interpolates the user into an f-string without parameter binding or escaping:
This pattern appears in numerous chart and dashboard query functions, including:
get_total_leads
get_ongoing_deals
get_average_ongoing_deal_value
get_won_deals
get_average_won_deal_value
get_average_deal_value
get_average_time_to_close_a_lead
get_average_time_to_close_a_deal
get_sales_trend
get_forecasted_revenue
get_funnel_conversion
get_deals_by_stage_*
get_lost_deal_reasons
get_leads_by_source
get_deals_by_source
get_deals_by_territory
get_deals_by_salesperson
PoC
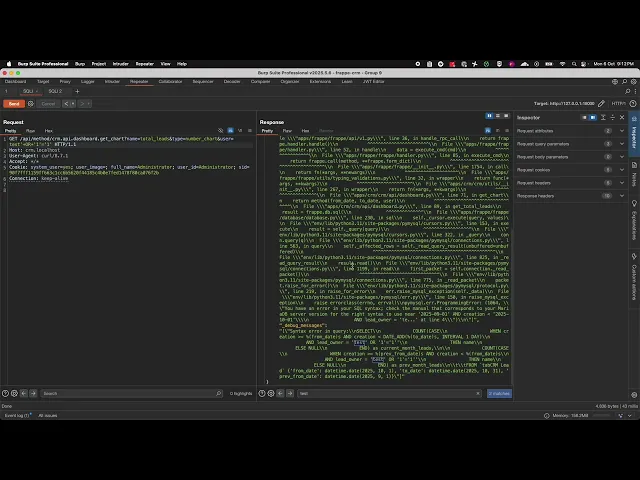
Error-based confirmation: Returns 500 with MariaDB syntax error referencing
AND lead_owner = ''inside the rendered SQL.Logic manipulation:
Evidence of Exploitation
crm.api. dashboard.get_chart endpoint:
crm.api.dashboard.get_dashboard endpoint:
Our security policy
We have reserved the ID CVE-2025-11461 to refer to this issue from now on.
System Information
Frappe CRM
Version 1.53.1
Operating System: Any
References
Github Repository: https://github.com/frappe/crm
Security: https://frappe.io/security
Mitigation
An updated version of Frappe CRM is available at the vendor page.
Credits
The vulnerability was discovered by Cristian Vargas from Fluid Attacks' Offensive Team.
Timeline
Oct 6, 2025
Vulnerability discovered
Oct 7, 2025
Vendor contacted
Oct 7, 2025
Vendor replied
Oct 14, 2025
Follow-up with vendor
Oct 14, 2025
Vendor confirmed
Oct 28, 2025
Vulnerability patched
Nov 26, 2025
Public disclosure
Does your application use this vulnerable software?
During our free trial, our tools assess your application, identify vulnerabilities, and provide recommendations for their remediation.