AI code security assistance (ACSA)
Secure your code with AI-powered guidance
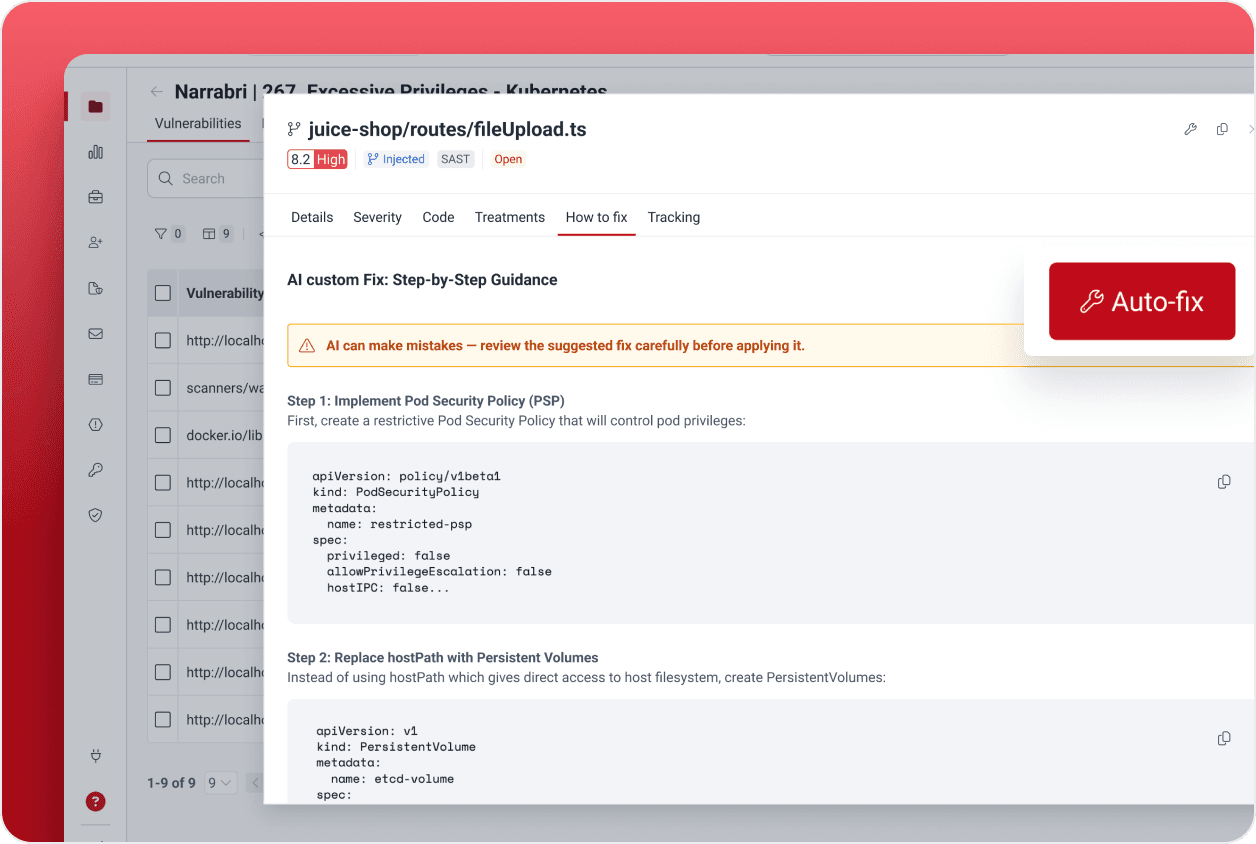
Context-aware fix suggestions that accelerate remediation
Real-time security guidance directly in the IDE and platform
Security for both human-written and AI-generated code

Companies already benefiting from Fluid Attacks' AI security solution
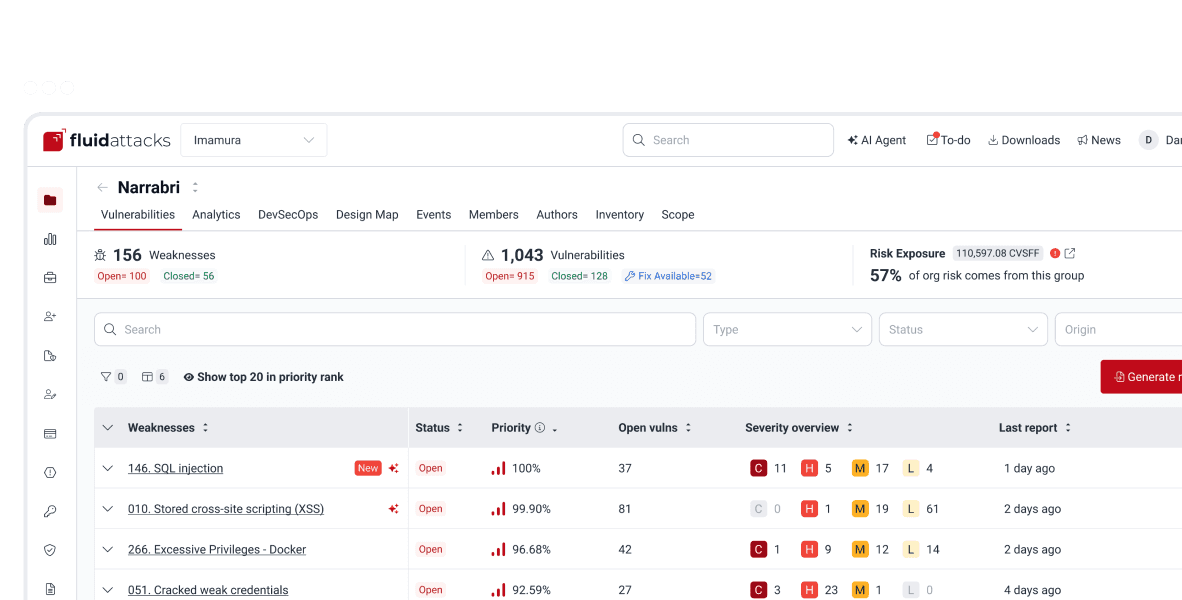
Why you should choose Fluid Attacks' ACSA solution
Frequently asked questions
What is AI code security assistance?
Can AI code security assistance scan code generated by GitHub Copilot or ChatGPT?
Does AI code security assistance work with my IDE?
Why is AI-generated code a security concern?
How do I know if my AI-generated code is secure?
What is the difference between Autofix and Custom Fix?
Can I get human support when AI suggestions aren't enough?
Do you want to learn more about AI code security assistance?
Read some of our posts related to this solution.
ACSA is a crucial piece of Fluid Attacks' solution
We offer an all-in-one solution that combines our AI, automated tools and pentesters to help you improve your cybersecurity posture continuously.