Svelte 5.46.0 - Hydratable Key Script-Breakout XSS (SSR)
5.3
Medium
Discovered by

Offensive Team, Fluid Attacks
Summary
Full name
Svelte 5.46.0 - Hydratable Key Script-Breakout XSS (SSR)
Code name
State
Public
Release date
Jan 15, 2026
Affected product
svelte
Vendor
sveltejs
Affected version(s)
>=5.46.0, <=5.46.3
Fixed version(s)
5.46.4
Package manager
npm
Vulnerability name
Reflected cross-site scripting (XSS)
Vulnerability type
Remotely exploitable
Yes
CVSS v4.0 vector string
CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:P/VC:N/VI:N/VA:N/SC:L/SI:L/SA:N
CVSS v4.0 base score
5.3
Exploit available
No
CVE ID(s)
Description
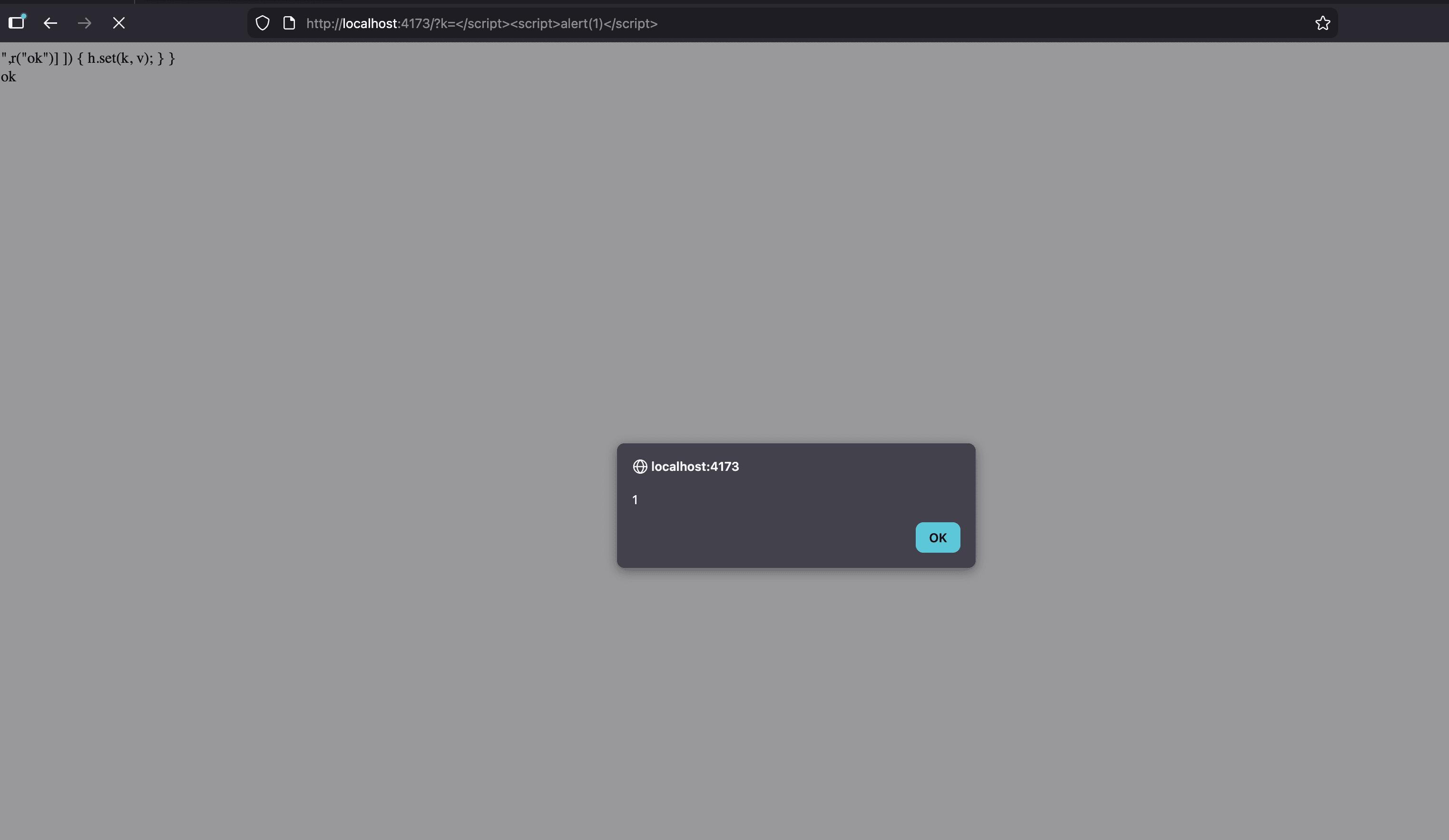
An SSR XSS exists in async hydration when attacker‑controlled keys are passed to hydratable. The key is embedded inside a <script> block without HTML‑safe escaping, allowing </script> to terminate the script and inject arbitrary JavaScript. This enables remote script execution in users' browsers, with potential for session theft and account compromise.
Vulnerability
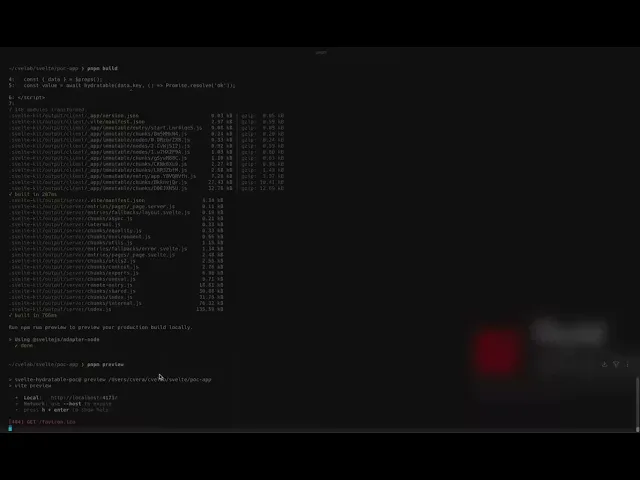
The vulnerability arises when hydratable(key, fn) accepts untrusted keys, which are then serialized into a <script> block in the server-rendered head without escaping unsafe characters. A malicious key containing </script> breaks out of the script context and injects arbitrary JavaScript into the HTML response.
File: packages/svelte/src/internal/server/renderer.js
Function: Renderer.#hydratable_block(ctx)
Sink: inline <script> payload that sets window.__svelte.h map.
JSON.stringify does not escape <, so a key containing </script> terminates the <script> tag.
Evidence of Exploitation
Our security policy
We have reserved the ID CVE-2025-15265 to refer to this issue from now on.
System Information
Svelte
Version >=5.46.0, <=5.46.3
Operating System: Any
References
Github Repository: https://github.com/sveltejs/svelte
Patch: https://github.com/sveltejs/svelte/releases/tag/svelte%405.46.4
Github Advisory: https://github.com/sveltejs/svelte/security/advisories/GHSA-6738-r8g5-qwp3
Mitigation
An updated version of Svelte is available at the vendor page.
Credits
The vulnerability was discovered by Camilo Vera from Fluid Attacks' Offensive Team.
Timeline
Dec 27, 2025
Vulnerability discovered
Dec 29, 2025
Vendor contacted
Jan 5, 2026
Vendor replied
Jan 5, 2026
Vendor confirmed
Jan 15, 2026
Vulnerability patched
Jan 15, 2026
Public disclosure
Does your application use this vulnerable software?
During our free trial, our tools assess your application, identify vulnerabilities, and provide recommendations for their remediation.







