Opinions
How to get into the top 10 at HTB Business CTF


Head of Research
Updated
Jan 21, 2026
5 min
The war had always been there, lurking in the shadows. The Volnaya Empire, a nation built on espionage and authoritarianism, set its master plan in motion: Operation Blackout, a covert offensive designed to cripple critical infrastructure and plunge rival nations into a terrifying new dark age.
With power grids and global financial systems under imminent threat, the world needed a last line of defense. And so, Task Force Phoenix was assembled—an elite group of hackers with a single mission: Take down the Volnaya Empire once and for all!
At Fluid Attacks, we answered the call and jumped straight into the heart of Task Force Phoenix. Over 4 days of intense operations, we deployed our best exploits, cracked heavy encryption, and seized control of entire Active Directory environments. When the digital smoke cleared, our banner flew high: we ranked #1 in Latin America and #9 worldwide. Proof that Latin America can step onto the global stage and compete through discipline, hard work, and teamwork.
This was the scenario we lived during the Global Cyber Skills Benchmark, better known as the Hack The Box Business CTF 2025, one of the most prestigious cybersecurity competitions in the world for corporate teams.
What is the HTB Business CTF?
The HTB Business CTF is a Jeopardy-Cloud-Fullpwn-style capture the flag: a competition where participants work in teams to solve challenges sorted by category and difficulty. There are specific challenges for web hacking, cryptography, reversing, and more, including key categories like cloud hacking (with challenges in AWS, for example) and fullpwn, where you need to fully compromise a server or an Active Directory (computer network) environment. This global corporate CTF is organized by Hack The Box, the well-known cybersecurity learning platform. In 2025, it drew 795 corporate teams with up to 30 players each, totaling 4,549 participants solving challenges across 16 cybersecurity categories or areas over 96 continuous hours.
The prizes
The top three teams took home the equivalent of $50,000 in Hack The Box products and services. First place went to Synacktiv from France, winning around $21,750 in prizes, including a secret HTB trophy, six months of BlackSky access for each player (HTB's Cloud Hacking Labs for Business), and $100 in exclusive swag or merch per player. Second place, GMO Cybersecurity from Japan, won roughly $16,200: each player received a pentesting certification by HTB known as CPTS, plus $50 in swag. Third place, Downscope from the U.S., won about $12,050: each player got six months of access to HTB's dedicated labs and $25 in swag.
How we built our team
To select the team that would represent Fluid Attacks in 2025, we first set some ground rules:
Full commitment from Friday, May 23rd through Tuesday, May 27th, at minimum from 8 AM to noon and 1 PM to 9 PM
Follow the event rules and compete with integrity
Use the brand of Fluid Attacks wherever possible
Automatically log hours spent on the competition using tracking software
Stay in constant communication with the team
Of course, along with the rules came some perks:
Six paid days off for all team members
Full access to company resources: computers, licenses, AWS, and more
A set budget for meals during the event
A coworking space for the team
With the rules and benefits in place, we sent out an invite to the entire hacking team, asking each person to rank their top 5 strongest categories where they could participate. Two coordinators then selected the team based on certifications, hacking experience, and internal metrics, assigning each participant 1 or 2 categories. After sharing the assignments and making adjustments, we ended up with a 14-player team covering every known category in the competition. In numbers, the team had: 41 unique hacking certifications, an average of 6 certifications per person; 521 total months of experience (working at Fluid Attacks), an average of 35 months per person; 25 reported CVEs total, an average of 2 CVEs per person; an average of 41 HTB machines solved per person, and an average of 26 HTB challenges solved per person.
Our journey through the competition
This wasn't our first time competing in an HTB Business CTF, but it was the first time we did it in a structured, organized way. In 2021, the competition's first edition, we placed #80 worldwide. In 2024, we climbed 45 spots to #35. And in 2025, we jumped another 26 positions to finish #9 worldwide. We did this with half the players allowed compared to the top 5 teams (who each had nearly 30 players), logging 754 total hours as a team—an average of 47 tracked hours per player.
The challenges we conquered
Out of 66 challenges, we completed 59, which demanded attacks that ranged from blind web vulnerabilities combined with cross-site scripting (XSS), to firmware deobfuscation and virtual machine reverse engineering in the Reversing category. We conducted from memory rootkit analysis in Forensics to USB traffic analysis in Hardware. And from Docker escapes chaining multiple CVEs in FullPwn to undergassing attacks in Blockchain. All the competition challenges and their solutions are available in HTB's official writeups.
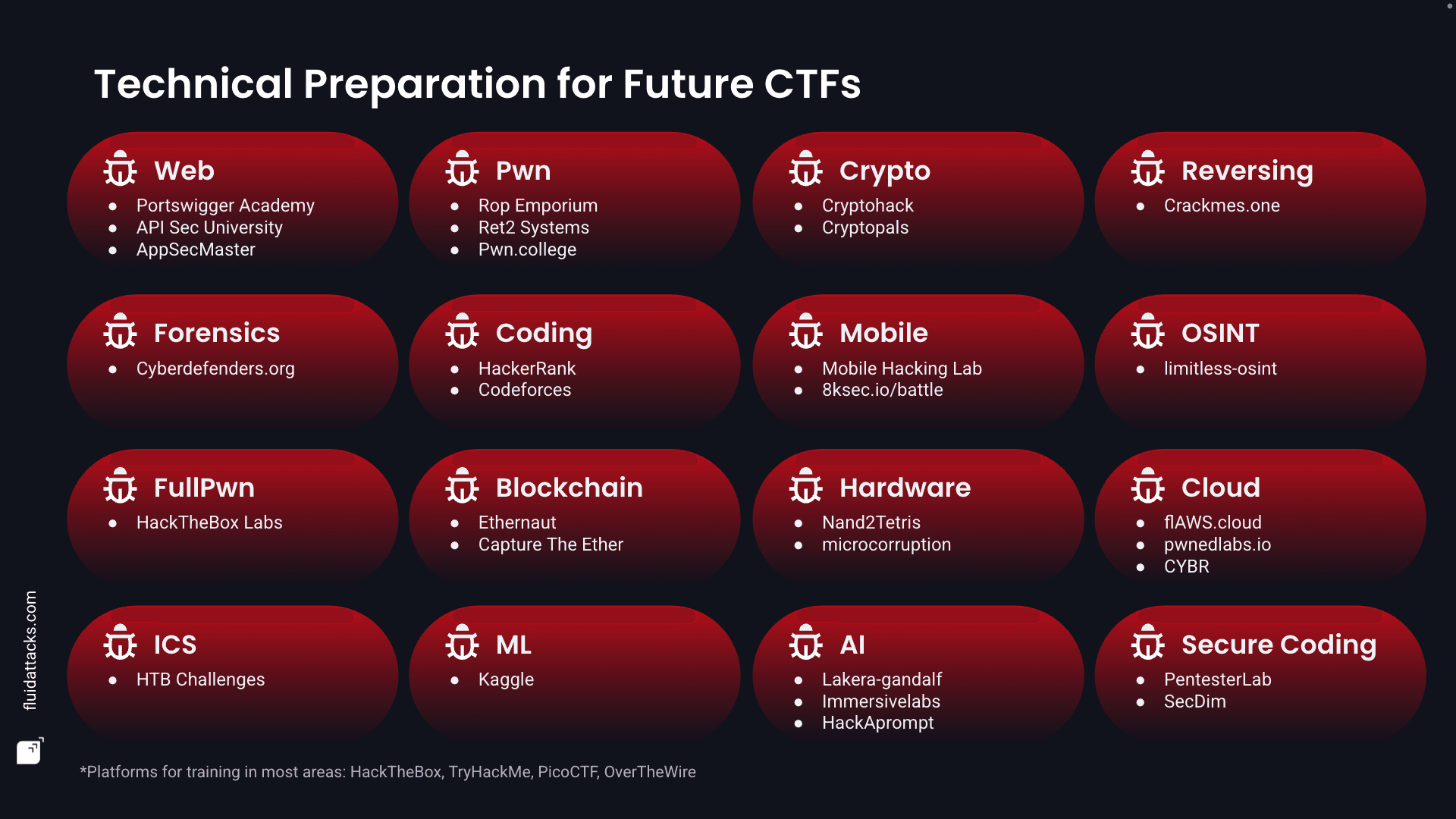
Training platforms
As part of preparing for this competition and the next, we compiled a list of platforms that can help with technical prep for future CTFs:
The keys to our success
Beyond technical preparation, here are the keys to our success:
Full dedication for the four days of competition: We set aside work responsibilities and even personal matters to fully immerse ourselves.
Effective collaboration: While each player has their own specialty and strengths, we realized we're capable of more when we work together.
Rest management: Resting was just as important as staying focused.
And of course, remembering that a CTF is also a game—the point is to enjoy it and compete.
It's not just about technical skills. The soft skills that drove our success were teamwork, humility, and clear communication. That said, we also recognize there's room for improvement.
What we'll improve
Regular training by competing in CTFs consistently as a team
Earlier preparation by sending out the team invite well in advance
Category-specific training, continuing individual prep in our respective areas of expertise
Open invitations, including everyone who wants to take on the challenge, not just the hacking team
Informing of attempted challenges using HTB's platform or whatever is available to keep the team in sync
Studying past writeups as a form of training
Two players per category plus two floaters to strengthen our approach to specific challenges and facilitate prompt help for the harder ones
Optimizing in-person collaboration, encouraging team sync-ups when possible, whether through a coworking space, an Airbnb, or a hotel
Onward to the next battle
Operation Blackout has been neutralized and Task Force Phoenix completed its mission, but wars in cyberspace never truly end. New threats will emerge, new empires will try to turn off the lights, and when that moment comes, we'll be ready. Better prepared, synchronized, and organized.
Because in Latin America, we don't just answer the call, we stay ahead of it.
See you at the next CTF.
Get started with Fluid Attacks' PTaaS right now
Other posts



















