Capture the flag (CTF) competitions
Remember playing capture the flag as a kid? Two teams, a field, and the adrenaline of sneaking into enemy territory to grab that precious piece of fabric. Cybersecurity borrowed that concept and turned it into one of the most effective ways to sharpen hacking skills without ending up on the wrong side of the law.
CTF meaning in cybersecurity
In cybersecurity, a CTF (capture the flag) is a competition where participants solve challenges to find hidden strings of text called "flags." These flags are tucked away in intentionally vulnerable programs, websites, or systems, and retrieving them requires applying real security knowledge. A flag might look something simple like flag{you_found_me} or follow a format specified by the organizers.
Participants work alone or in teams to discover as many flags as possible within a set timeframe, which can range from a few hours to several days. Points stack up based on the number of flags captured and the difficulty of each challenge. The individual or team with the most points at the end wins, sometimes walking away with cash prizes, recognition, or both.
Types of CTF competitions
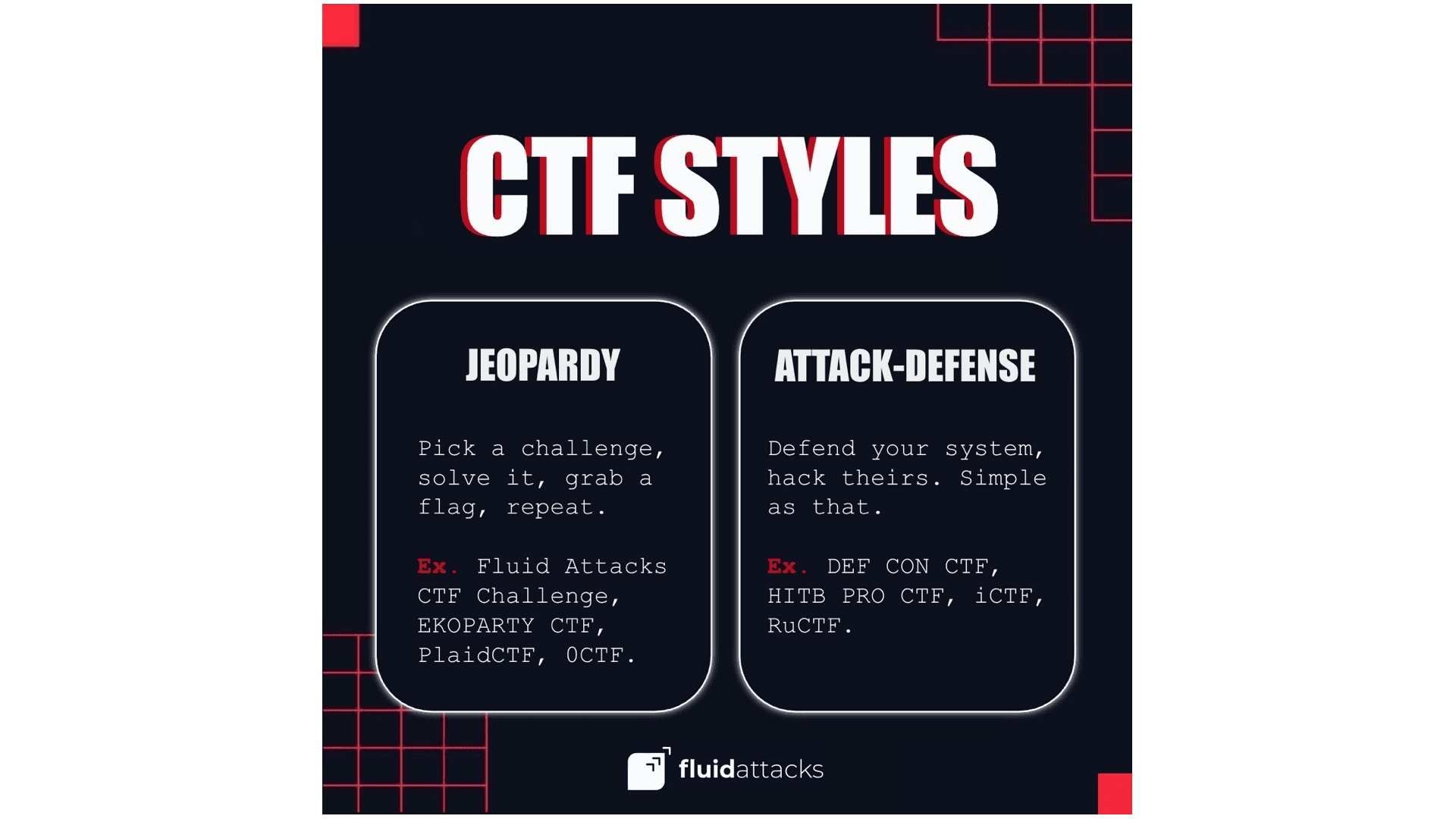
CTFs generally fall into two main categories: Jeopardy-style and Attack-Defense.
Jeopardy-style CTFs present a series of challenges across different categories. Participants pick a challenge, solve it, retrieve the flag, and move on to the next one. Categories typically include web exploitation, cryptography, reverse engineering, forensics, and steganography. Each challenge has a point value tied to its difficulty; the harder the puzzle, the bigger the reward. This format is common for online events and works well for beginners since you can choose challenges that match your skill level. Well-known Jeopardy-style competitions include Google CTF, PlaidCTF (organized by Carnegie Mellon's Plaid Parliament of Pwning), HITCON CTF, and 0CTF.
Attack-Defense CTFs get closer to the original outdoor game. Each team receives a vulnerable system to defend while simultaneously trying to compromise the systems of opposing teams. You earn points both for patching your own vulnerabilities and for successfully exploiting others. This format demands strong teamwork and quick thinking since you're playing offense and defense at the same time. The DEF CON CTF finals are probably the most famous example of this style, often called the "World Series of hacking." RuCTF, organized by Russia's HackerDom team, is another prominent Attack-Defense competition.
Some competitions blend both styles, creating a mixed format that tests a broader range of skills.
Challenge categories you'll encounter
CTF challenges cover a wide spectrum of security disciplines. Web exploitation tasks involve finding and leveraging vulnerabilities in web applications, from SQL injection to cross-site scripting. Cryptography challenges require breaking ciphers or analyzing encryption algorithms. Reverse engineering presents you with binaries that you need to dissect to understand how they work. Forensics challenges might hand you a memory dump or network capture file and ask you to extract hidden data. Steganography hides flags inside images, audio files, or other media.
This variety is intentional. Real-world security work rarely fits into a single box, and CTFs reflect that reality.
Why CTFs matter
Beyond the thrill of competition, CTFs serve as a practical training ground. They let you apply theoretical knowledge to hands-on scenarios in a legal, controlled environment. Many security professionals credit CTFs with accelerating their learning far beyond what textbooks and courses alone could achieve.
CTFs also function as networking hubs. You meet people who share your interests, learn from how others approach problems, and sometimes catch the attention of recruiters. Several major tech companies and security firms actively scout talent at prominent CTF events; a strong showing can open doors.
For students and career-changers, CTFs provide a way to build credible experience. Finishing well in recognized competitions signals to employers that you can actually do the work, not just talk about it.
Where to find CTF competitions
CTFtime tracks CTF events worldwide, listing upcoming competitions along with their formats, dates, and registration links. The site also assigns a "weight" metric to each event, reflecting its difficulty on a scale from 0 to 100. Higher weights mean tougher challenges and stiffer competition; if you're just getting started, filtering for lower-weight events can help you find competitions that match your current skill level without throwing you into the deep end.
Major conferences like DEF CON and BSides host flagship CTFs that draw participants from across the globe. Academic teams, security companies, and government agencies all run their own events throughout the year.
If you're looking for CTFs in Latin America, consider participating in Ekoparty (Argentina), JCUN and DragonJARCON (Colombia), PWNEDCR (Costa Rica), 8.8 (all over), and, of course, Fluid Attacks' CTF Challenge (all over).
For those just starting out, platforms like PicoCTF, TryHackMe, and Hack The Box offer beginner-friendly challenges that you can tackle at your own pace. We recommend using these platforms to train as well. Actually, in our blog post "How to get into the top 10 at HTB Business CTF" you can see our extended list where you can see the options by categories.
Also, we put together a top 10 international CTF competitions post a while back. It's honestly overdue for a refresh, so keep an eye out for an updated ranking soon.
Fluid Attacks CTF Challenge
We've competed in our share of CTFs over the years, and now we host our own. The most recent, Fluid Attacks' CTF - LATAM Challenge ran for 24 hours, inviting security professionals, pentesters, red teamers, students, and enthusiasts to test their skills against a series of real-world-inspired challenges.
Participants discovered and exploited vulnerabilities to retrieve flags, submitted them through the platform, and watched their scores climb on the leaderboard. The competition rewarded the winner with USD 1,000 and invaluable experience.
Whether you're looking to sharpen existing skills or push yourself into unfamiliar territory, CTFs offer a path forward. Find an event that fits your level, assemble a team or go solo, and start capturing flags.











