MacForge 1.2.0 Beta 1 - Local Privilege Escalation
Discovered by

Offensive Team, Fluid Attacks
Summary
Full name
MacForge 1.2.0 Beta 1 - Local Privilege Escalation via Insecure XPC Service
Code name
State
Public
Release date
3 oct 2025
Affected product
MacForge
Vendor
Mac Enhance
Affected version(s)
1.2.0 Beta 1
Vulnerability name
Privilege escalation
Vulnerability type
Remotely exploitable
No
CVSS v4.0 vector string
CVSS:4.0/AV:L/AC:L/AT:N/PR:L/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N
CVSS v4.0 base score
8.5
Exploit available
Yes
CVE ID(s)
Description
MacForge version 1.2.0 for macOS contains an insecure XPC service that allows local, unprivileged users to escalate their privileges to root. The vulnerability stems from the XPC service com.macenhance.MacForge.Injector.mach, which exposes a method installFramework:atlocation:withReply:. This method can be invoked by any local user without authentication or authorization checks.
An attacker can abuse this method to perform arbitrary file copy operations to any location on the filesystem with root privileges. The resulting file's permissions are the same as the original file. But by chaining this powerful primitive with the standard behavior of the macOS newsyslog utility, an attacker can create a malicious sudoers configuration file, granting them full, passwordless root access.
Vulnerability
The core of the vulnerability lies in the MFInjectorProtocol XPC interface, which does not validate the client connecting to it, allowing any local process to invoke its methods. The installFramework method, intended for installing application frameworks, fails to validate its input paths, effectively becoming an arbitrary file copy function running as root.
This allows a local attacker to:
Exploit 1:
Write arbitrary files to sensitive system locations.
Leverage this file-write primitive to create a malicious newsyslog configuration.
Trigger newsyslog to create a root-owned file with attacker-controlled content.
Place this file in /etc/sudoers.d/ to gain permanent root privileges.
Exploit 2:
Overwrite /etc/paths to add a path to a directory controlled by the attacker and hijack system binaries. (require user interactions)
Overwrite the /etc/hosts file to redirect the traffic to a malicious server. (require user interactions)
PoC
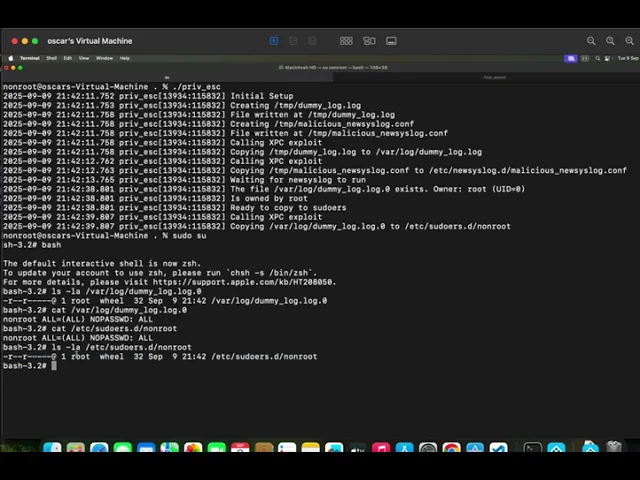
The following Proof of Concept (PoC) demonstrates the escalation from a standard user to root. It is implemented in Objective-C and requires compilation with the Foundation framework.
Evidence of Exploitation
Compile the exploit:
Run the exploit:
Trigger newsyslog: The exploit will wait for the automatic execution of newsyslog (which happens hourly by default on macOS). To accelerate, the attacker can manually trigger it from another terminal:
Verify privileges: Once the exploit completes, the user nonroot will have passwordless sudo access.
Newsyslog logs (executed each hour)

Exploit

Newsyslog config added

/var/log/dummy_log.log.0 permissions and content after rotated.

Our security policy
We have reserved the ID CVE-2025-10751 to refer to this issue from now on.
System Information
MacForge
Version 1.2.0 Beta 1
Operating System: Mac
References
Github Repository: https://github.com/MacEnhance/MacForge
Mitigation
There is currently no patch available for this vulnerability.
Credits
The vulnerability was discovered by Oscar Uribe from Fluid Attacks' Offensive Team.
Timeline
9 sept 2025
Vulnerability discovered
19 sept 2025
Vendor contacted
3 oct 2025
Public disclosure
Does your application use this vulnerable software?
During our free trial, our tools assess your application, identify vulnerabilities, and provide recommendations for their remediation.







