i-Educar 2.10.0 - Stored Cross-Site Scripting (XSS) in admin panel
4,8
Medium
Discovered by
External Pentester
Summary
Full name
i-Educar 2.10.0 - Stored Cross-Site Scripting (XSS) in matricula_interna parameter of educar_usuario_cad.php
Code name
State
Public
Release date
9 dic 2025
Affected product
i-Educar
Vendor
Portabilis
Affected version(s)
2.10.0
Vulnerability name
Stored cross-site scripting (XSS)
Vulnerability type
Remotely exploitable
Yes
CVSS v4.0 vector string
CVSS:4.0/AV:N/AC:L/AT:N/PR:H/UI:P/VC:N/VI:N/VA:N/SC:L/SI:L/SA:N
CVSS v4.0 base score
4.8
Exploit available
Yes
CVE ID(s)
Description
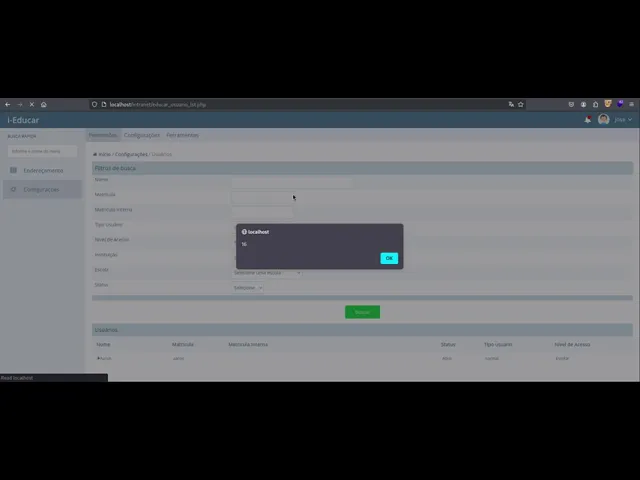
A Stored Cross-Site Scripting (XSS) vulnerability was identified in the educar_usuario_cad.php endpoint of the i-Educar application. The issue arises because the matricula_interna parameter is not sanitized before being stored in the database. Malicious scripts injected into this field persist in the system and are executed whenever the affected record is displayed in the web interface, leading to a persistent client-side compromise.
Vulnerability
The application fails to properly validate or encode user input in the Matrícula Interna field (matricula_interna). An attacker can inject arbitrary JavaScript code into this field, which is stored in the backend database. Whenever the admin later views the affected record, the malicious payload executes in their browser context.
It is important to note that this vulnerability works from admin to admin. Administrator permissions are required, and it only affects other users with access to the administrative panel.
PoC
Steps to reproduce:
Log in with an account that can create or edit users.
Navigate to Configurações → Permissões → Usuários
Create a new user or edit an existing one.
In the Matrícula Interna field, insert the payload
Save changes.

Open the affected user record.
The payload executes immediately, confirming the stored XSS.
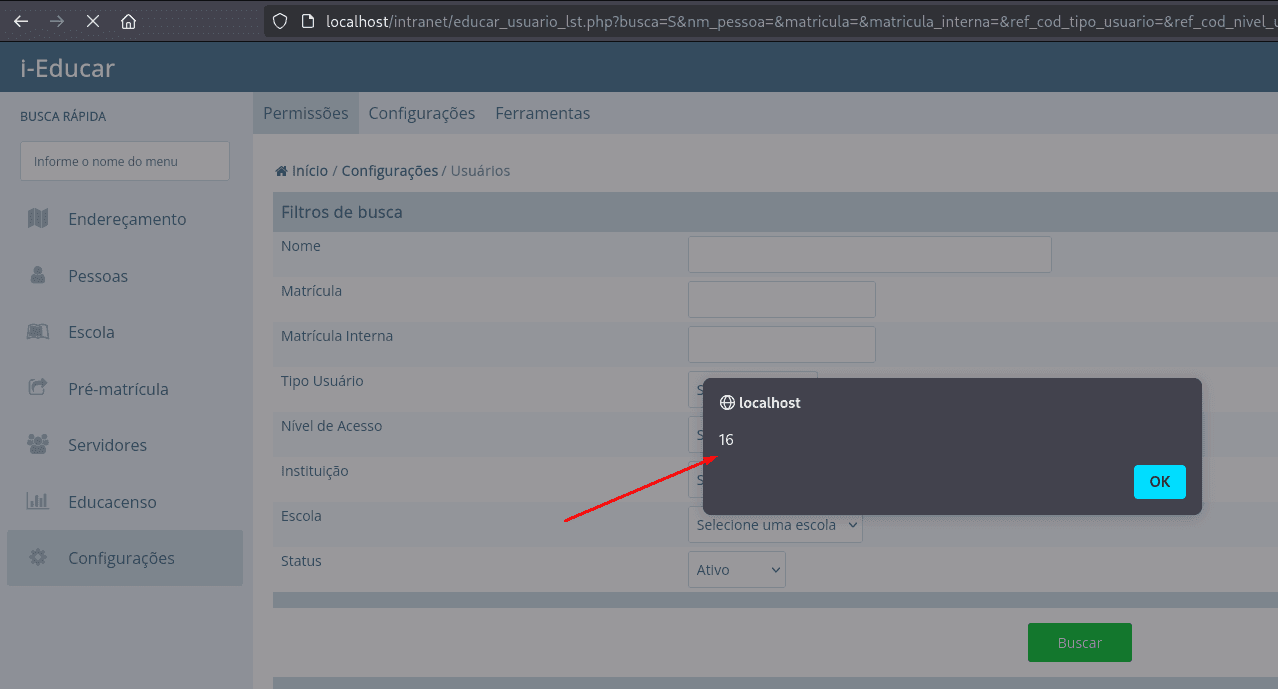
Evidence of Exploitation
Our security policy
We have reserved the ID CVE-2025-9638 to refer to this issue from now on.
System Information
i-Educar
Version 2.10.0
Operating System: Any
References
Github Repository: https://github.com/portabilis/i-educar
Credits
The vulnerability was discovered by Marcelo Queiroz, an independent security researcher.
Timeline
10 ago 2025
Vulnerability discovered
1 sept 2025
Vendor contacted
9 sept 2025
Vendor replied
15 sept 2025
Follow-up with vendor
9 dic 2025
Public disclosure
Does your application use this vulnerable software?
During our free trial, our tools assess your application, identify vulnerabilities, and provide recommendations for their remediation.







