Philosophy
OWASP Top 10 2025 wants a word with your supply chain


Content writer and editor
Updated
Jan 14, 2026
6 min
The Open Worldwide Application Security Project (OWASP) Top 10 has been the go-to awareness document for developers and security professionals since it first appeared. More than just a list, it has become one of the most cited requirement documents for software application security. Organizations around the world use it as a baseline for security testing, compliance frameworks like PCI DSS reference it, and security teams everywhere structure their training around it.
Four years after the last update, OWASP has released the official 2025 edition, and it reflects a fundamental shift in how we think about application security. The new top makes clear that writing secure code isn't enough. With supply chain risk debuting at number three and misconfigurations climbing to second place, organizations must now think beyond their own codebase to the entire ecosystem that builds, configures, and delivers their software.
Also, there is a brand new addition to the list. Excited to know what it is? Let's dive in.
The numbers don't lie (and there are a lot more of them)
The 2025 edition analyzed a staggering 589 Common Weakness Enumerations (CWEs), up from roughly 400 in 2021. This nearly 50% increase reflects the growing complexity of modern software systems and the expanding attack surface that comes with it. Data was donated from varied sources and referred to over 2.8 millions applications.
The methodology continues to blend data-driven analysis with community insights. Two categories are voted in by practitioners on the front lines, ensuring that emerging risks make the cut even if they haven't yet shown up in automated testing data. After all, by the time researchers develop testing methodologies and integrate them into tools, years may have passed.
The new order is the following, where you can see the aforementioned voted-in items ("Software Supply Chain Failures" and "Security Logging & Alerting Failures").
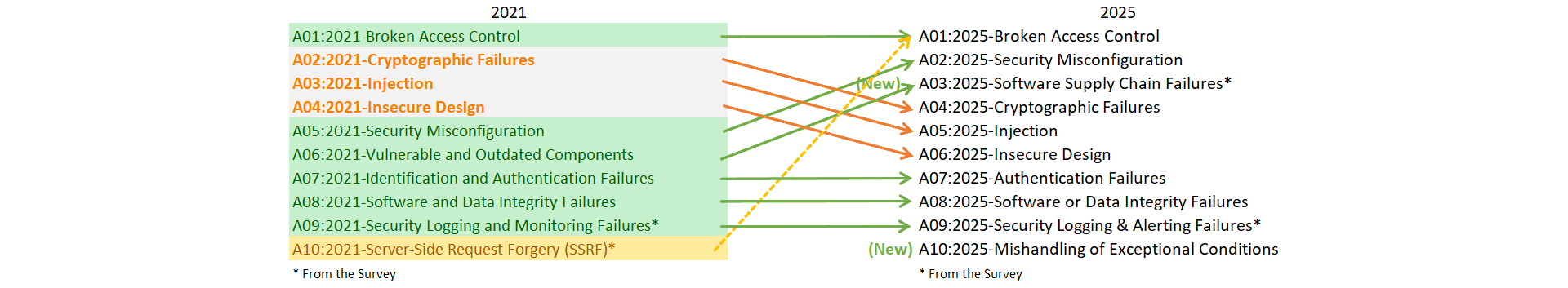
OWASP Top 10 2021 and 2025 comparison (taken from owasp.org)
Access control: Still broken, still #1
Broken Access Control maintains its position at number one. On average, around 4% of applications tested had one or more of the 40 CWEs in this category. That might sound small, but when you consider the scale of modern software deployment, it translates to millions of vulnerable applications.
The big news here is the absorption of Server-Side Request Forgery (SSRF), which was a standalone, voted-in category in 2021. SSRF has been rolled into Broken Access Control because, in modern applications built on microservices and cloud APIs, the line between service-level and user-level access has become increasingly blurry. An SSRF vulnerability is fundamentally an access control failure, as it allows attackers to make requests they shouldn't be authorized to make.
Misconfiguration moves up (way up)
Security Misconfiguration made an aggressive climb from fifth place in 2021 to second in 2025. This shouldn't surprise anyone who has spent time in modern cloud environments. As software engineering continues to shift more application behavior into configuration files, cloud permissions, and infrastructure templates, every mis-set flag becomes a potential security catastrophe.
The category now encompasses 16 CWEs and was found in 3% of tested applications. It covers the usual suspects: exposed default accounts, unnecessary services, insecure permissions, missing security headers, and the ever-popular misconfigured cloud storage buckets that seem to make headlines every other week. XML External Entities (XXE) remains consolidated here, recognizing that XXE is fundamentally a configuration problem.
Maybe it's okay to have trust issues
The most significant structural change in the 2025 edition is the transformation of Vulnerable and Outdated Components into Software Supply Chain Failures. This isn't just a rebrand but also a complete expansion of scope that acknowledges an ever clearer reality, which is modern applications are assemblies of external code.
The attacks that drove this change are, to name a few, SolarWinds in 2020, Codecov in 2021, the ua-parser-js npm hijacking that same year, Log4j's explosive debut, and the xz Utils backdoor in 2024. Each incident demonstrated that attackers don't need to find vulnerabilities in your code when they can simply compromise the code you trust.
This category now covers the entire software ecosystem: dependencies, build systems, and distribution infrastructure. It forces organizations to ask uncomfortable questions about their CI/CD pipelines, artifact provenance, and whether they really know who has push access to their package repositories.
The middle of the pack still packs a punch
Cryptographic Failures dropped from second to fourth place, but don't let the slide fool you, as improper encryption and key management remain critical risks. This category encompasses everything from using outdated algorithms to leaking cryptographic keys in logs or error messages.
Injection falls two spots to number five, finally abandoning the top 3. It still includes Cross-Site Scripting (XSS) and covers 38 CWEs with the greatest number of associated CVEs. The drop reflects progress in defensive measures like parameterized queries and output encoding, but injection remains a stubborn problem wherever code and data mix.
Insecure Design slides to sixth place from being introduced and given high importance in 2021. This category pushes organizations to think about security way earlier in the development process. The good news is the industry has made noticeable improvements in threat modeling and secure design practices. The position change suggests that message is getting through.
Same spot, same problems
Authentication Failures holds steady at seventh place with a slight name change (previously Identification and Authentication Failures). The 36 CWEs in this category cover everything from weak password policies to session management flaws. The stability suggests that while multi-factor authentication and improved password practices have helped, the problem persists.
Software or Data Integrity Failures continues at eighth place, focusing on situations where systems trust code or data without verifying provenance. This includes unsigned updates, unvetted plugins, and CI/CD pipelines that accept artifacts without integrity checks. It's distinct from the broader supply chain category because it zeros in on integrity verification at the artifact and data level.
Security Logging and Alerting Failures retains its position at ninth place with an important addition to its name: alerting. OWASP now explicitly emphasizes that great logging with no alerting is of minimal value. You can have petabytes of beautifully formatted logs, but if nobody gets woken up at 3 AM when something suspicious happens, those logs are just expensive storage.
This category will always be underrepresented in testing data because you can't scan for the absence of detective controls the way you can scan for an SQL injection. It was again voted into position by community survey participants who understand that without proper logging and alerting, attacks and breaches simply cannot be detected in time.
Failing safely is now a category
"OK, only one place left. This must be that new thing on the list?" Yup. The completely new addition to the 2025 list is Mishandling of Exceptional Conditions at number ten. This category has been lurking just outside the OWASP Top 10 for several years, and enough data combined with community support finally pushed it over the line.
The category contains 24 CWEs focusing on improper error handling, logical errors, failing open, and other scenarios that emerge when systems encounter unusual conditions. The issue is basically when an application (a) doesn't prevent unusual situations from happening, (b) doesn't identify them when they occur, or (c) responds poorly when they do.
This is particularly insidious because developers often focus testing on happy paths, meaning valid inputs and expected behaviors. But sophisticated attackers live in the edge cases, probing what happens when systems fail. When an application "fails open" instead of "failing secure," it can expose functionality or data that should remain protected.
OWASP's prevention guidance is straightforward: set limits everywhere. Rate limiting, resource quotas, and throttling help prevent exceptional conditions from occurring in the first place. When errors do happen, catch them where they occur rather than rely on high-level handlers later. Use strict input validation, centralized error handling, and—critically—design systems to fail closed rather than open. If a security check fails unexpectedly, the response should be to deny access, not grant it.
Testing from number 1 to 10
At Fluid Attacks, we help organizations tackle these challenges head-on through continuous security testing that combines AI-powered tools with expert human pentesters. Our Continuous Hacking solution addresses all OWASP Top 10 categories. It includes access control testing that uncovers privilege escalation paths, IaC analysis to catch misconfigurations before deployment, SCA that maps your dependency tree for supply chain risks, and everything down to error handling at number 10. Contact us to see how we can help you stay ahead of the threats that matter most.
Get started with Fluid Attacks' application security solution right now
Other posts



















