Nu Html Checker (validator.nu) - Restriction bypass vulnerability allowing local SSRF
6,9
Medium
Discovered by

Offensive Team, Fluid Attacks
Summary
Full name
Nu Html Checker (validator.nu) - Restriction bypass vulnerability allowing local SSRF via Arbitrary URL Fetching
Code name
State
Public
Release date
13 de jan. de 2026
Affected product
The Nu Html Checker (vnu)
Vendor
validator
Affected version(s)
latest
Vulnerability name
Server-side request forgery (SSRF)
Vulnerability type
Remotely exploitable
Yes
CVSS v4.0 vector string
CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:N/VI:N/VA:N/SC:L/SI:N/SA:N
CVSS v4.0 base score
6.9
Exploit available
Yes
CVE ID(s)
Description
Nu Html Checker (validator.nu) contains a restriction bypass that allows remote attackers to make the server perform arbitrary HTTP/HTTPS requests to internal resources, including localhost services. While the validator implements hostname-based protections to block direct access to localhost and 127.0.0.1, these controls can be bypassed using DNS rebinding techniques or domains that resolve to loopback addresses (e.g., localtest.me → 127.0.0.1).
The vulnerability affects the HTML5 validator service widely used by developers, CI/CD pipelines, and automated testing tools. The bypass allows attackers to access internal services that were intended to be protected by the localhost filtering.
Vulnerability
The vulnerability is exploitable through two attack vectors:
1. Direct SSRF via doc URL parameter
Simple GET request: http://validator.example.com/?doc=http://localtest.me:6379
Bypasses localhost protection using DNS that resolves to 127.0.0.1
Clickable link that can be shared via email, Slack, bug reports, or documentation
Automatically triggered by CI/CD pipelines that validate URLs
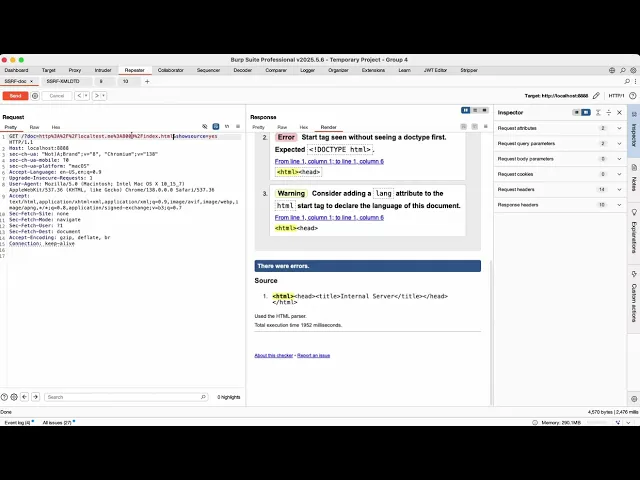
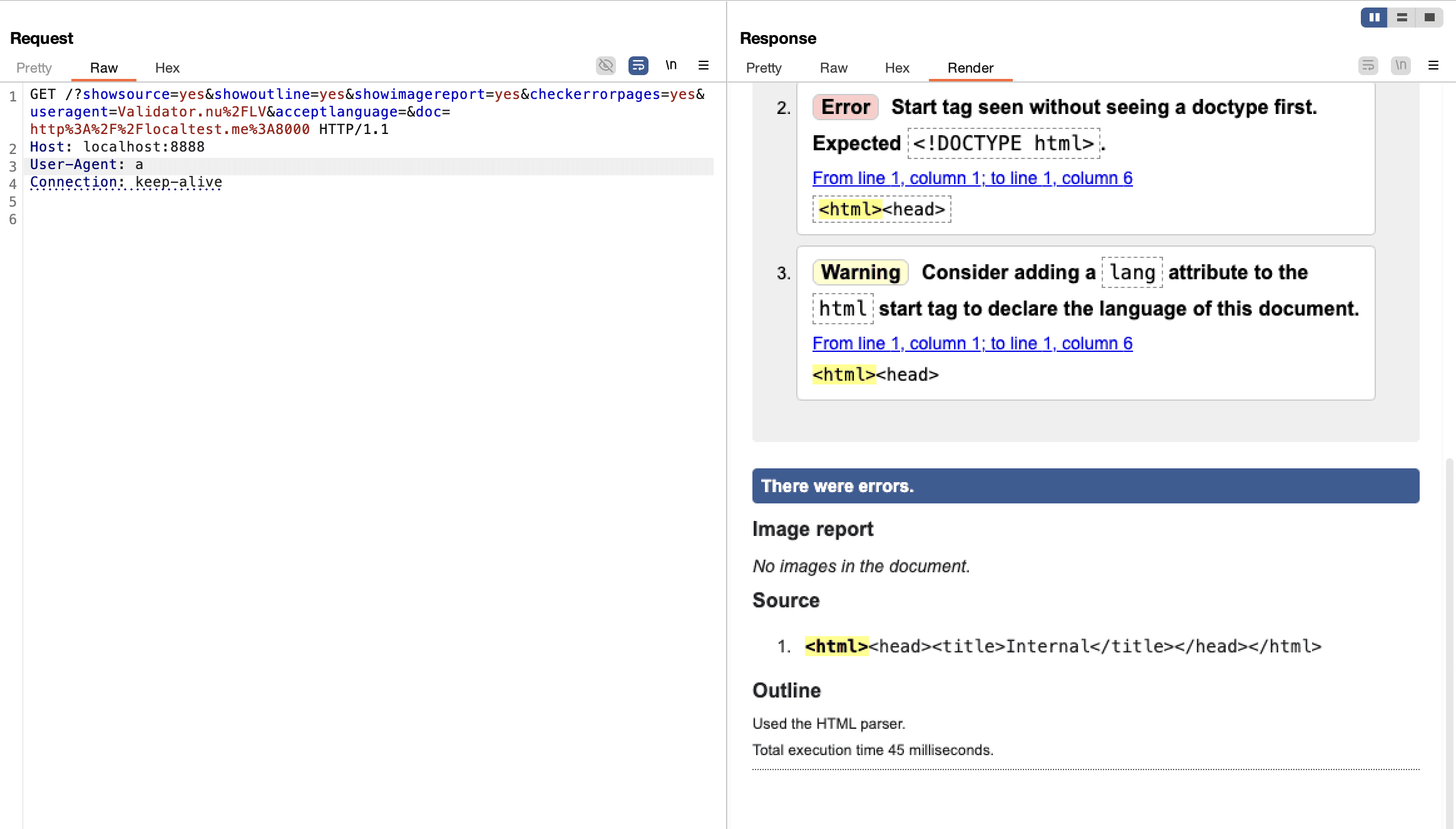
Example: http://localhost:8888/?doc=http%3A%2F%2Flocaltest.me%3A6379 (attacks Redis on localhost)
2. SSRF via XML External Entities (when using parser=xmldtd):
Leverages the XML DTD validation feature that allows external entities
Same DNS rebinding bypass applies: <!ENTITY xxe SYSTEM "http://localtest.me:6379/">
Used when the attacker controls the XML/HTML content being validated.
Both attack vectors share the same validator, which implements two security controls that are both insufficient
1. Hostname-based localhost blocking: Blocks strings like localhost and 127.0.0.1, but does not:
Resolve DNS before validation
Block domains that resolve to private/loopback IP addresses
Validate the final resolved IP address after DNS lookup
2. Port filtering: Only allows ports 80, 81, 443, and ports > 1024, but:
Most modern services run on high ports (Redis 6379, MySQL 3306, Elasticsearch 9200, etc.)
Web applications commonly use ports like 3000, 4200, 5000, 8000, 8080, 8888, 9000
Cloud metadata services use port 80 (169.254.169.254:80)
PoC
Evidence of Exploitation
Our security policy
We have reserved the ID CVE-2025-15104 to refer to this issue from now on.
System Information
The Nu Html Checker (vnu).
Version latest
Operating System: Any
References
Github Repository: https://github.com/validator/validator
Mitigation
There is currently no patch available for this vulnerability.
Credits
The vulnerability was discovered by Oscar Uribe from Fluid Attacks' Offensive Team.
Timeline
18 de dez. de 2025
Vulnerability discovered
26 de dez. de 2025
Vendor contacted
26 de dez. de 2025
Vendor replied
13 de jan. de 2026
Public disclosure
Does your application use this vulnerable software?
During our free trial, our tools assess your application, identify vulnerabilities, and provide recommendations for their remediation.







