| 5 min read
Table of contents
The current global situation with the coronavirus or COVID-19 has led
many of us to respond with our work from home. Amidst so much
uncertainty, there are many of us who could be looking for reliable
information on the progress of this pandemic, on what are the symptoms
and what tests are available, and how we can protect ourselves and our
families. It is claimed that this is being exploited by
scammers, and one of their
methodologies may easily be phishing, which we will discuss below.
Phishing can be understood as a social engineering tactic in which messages persuade the user to follow fraudulent web routes, to open attachments, or to reply to messages. All this generally to extract sensitive information. It is one of the most effective cyber threats, posing risks to government, industry, and all types of users. Millions of data breaches have resulted from the action of phishing. And billions of dollars are lost every year.
The term 'phishing' apparently originated in 1996 when hackers
stealing data from American accounts took "emails as 'hooks' to catch
their 'fish' from the 'sea' of internet
users". Victims
end up revealing confidential information about themselves, someone
else, or some entity to which they have access. Such information may
include passwords, bank account information, credit card numbers and
others.
Currently the attackers are going beyond emails. They are also making considerable use of social networks, "instant messaging applications, and online file-sharing services".
Beyond the extraction of information, malware (such as ransomware) can also be installed through these attacks. The attacker can then request money transfers or initiate unauthorized financial transactions. She can also lead to involuntary collaboration by the recipient to commit a scam within a company (perhaps the simplest means of entry).
Fraudulent emails—as part of a semantic attack— ask people for sensitive information to be revealed on fraudulent websites but with the appearance of authentic ones. So, if you are a Playstation user, for example, you may receive a supposed email from them presenting a false version of their website so that you can enter your credentials there. A good graphic design makes the user believe that the information is requested from a legitimate and recognized organization or brand. When in fact it is the creative work of a con artist. A site run by him or her.
Wait a minute, what do you mean by a semantic attack?
According to Downs, Holbrook, and Cranor (2006), computer security attacks can be divided into: physical, syntactic, and semantic. The first are aimed at the physical infrastructure of systems and networks. The second are directed at software. And the third, which is where we include phishing, are aimed at people. Semantic attacks are oriented to extract benefits from the way we humans interact with computer systems and the interpretation we make of messages.
Phishing can be quite cheap. Scams usually last a few days. Its infrastructure is then free of costs “imposed by many e-commerce trust systems”. Malicious individuals can easily acquire the necessary phishing kits from underground sites. Tens of thousands of those kits developed by mixing HTML and PHP are available today, living for about 36 hours or so before being detected and deleted.
In addition, phishers can be difficult to detect since they succeed in hiding the location of their servers. They have also begun to create networks of attackers, with each one doing a part of the attack. Sometimes even one of them just creates the tools, and ends up recruiting inexperienced phishers to collect all the information, be labeled as guilty, and get no benefits. That way, the real phisher could pass as undetected.
Some types of phishing and techniques
The attack can be individualized. So we’re talking about ‘spear phishing.’ The attacker collects (from profiles and blogs, for example) and uses information about a particular potential victim. While it can be a user, it can also be a group of employees from certain areas in an organization.
Another form of phishing is working with widespread information. In this case the attack network is much wider, hoping that among so many, at least some recipients will fall into the trap.
The criminals may lure the user through persuasive and realistic messages promising certain benefits (e.g., money, free products, job opportunities) or may simply force the user with specific threats. The phishers may seek to arouse fear, urgency, duty, greed or curiosity. They intend to provoke quick and impulsive decisions in the person.
There is also evidence of a type of phishing called whaling. In this case, rich and powerful individuals are targeted. Sometimes, contrary to attacking them directly, their identity and authority is used to extract financial information or funds from the organization they belong to. Alternatively, the use of other people’s identities can also involve those of trusted people such as family members, colleagues or friends.
Messages from phishers can have significant narrative force and connect with the reader through surprise. When the message is very long, the receiver may end up paying more attention to the characteristics of the design. Sometimes phishers use images from a legitimate hyperlink to direct us to a different, corrupt site. Other times they use fraudulent browser windows next to or above the legitimate ones.
Towards phishing prevention
Some users fail to distinguish between legitimate and fraudulent URLs,
and as Dhamija, Tygar, and Hearst
(2006)
illustrate, they may take www.ebay-members-security.com as belonging to
www.ebay.com. Or they may be misled by character substitutions such as
www.paypai.com, and www.paypa1.com, instead of the original
www.paypal.com.
Many users do not know or do not understand how the security indicators
in web browsers work. As with the closed padlock icon, in this case in
Chrome (in another browser it could be located elsewhere). This lock
indicates that the website we are on was delivered securely by SSL
(Secure Sockets Layer). A cryptographic protocol "used to provide
authentication and secure communications over the
Internet".
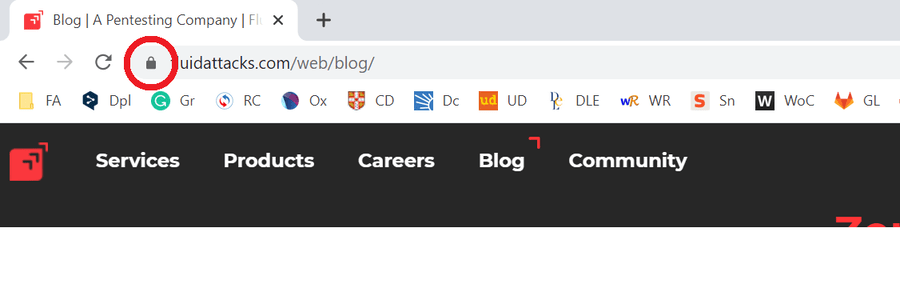
Security indicator on Chrome.
A system can be well equipped with firewalls, certificates, and encryption and authentication mechanisms, and phishing can be successful because of the user’s knowledge, attention, and decision-making. From here it is then suggested a greater understanding of the human and situational factors related to the success of phishing attacks.
In addition to technical support, many organizations try to provide guidance to users and employees. The idea of seeking help when a strange situation arises should be strengthened. Also, organizations should establish action plans in the presence of suspected phishing attacks.
In conclusion, and oriented towards a prevention of phishing attacks, here are just some of the tips you will find in the documents (which we recommend you review) from DHS and CPNI:
-
Check if message subjects are generic.
-
Consider that those messages may show unusual or significant spelling and grammar errors.
-
Have as a key what type and amount of information is being requested.
-
Be careful with messages that request urgent action.
-
If possible, try to contact the sender by another means of communication to verify the message.
Table of contents
Share
Recommended blog posts
You might be interested in the following related posts.












