| 3 min read
Table of contents
We already know what ransomware is: malicious software that, being on your computer, is capable of encrypting some of your important files, denying you access to them, or blocking your operating system completely. At the end of the day, we know that paying the ransom to the criminal groups does not guarantee that they will give you the decryption key to unlock your data. Ransomware attacks are increasing year after year. In 2020 the victim count in the USA was 2,474; an increase of over 20% from 2019 and over 65% from 2018 (see image below). To understand why this is happening, we must refer to the change in the attack model and explain what Ransomware as a Service (RaaS) is.
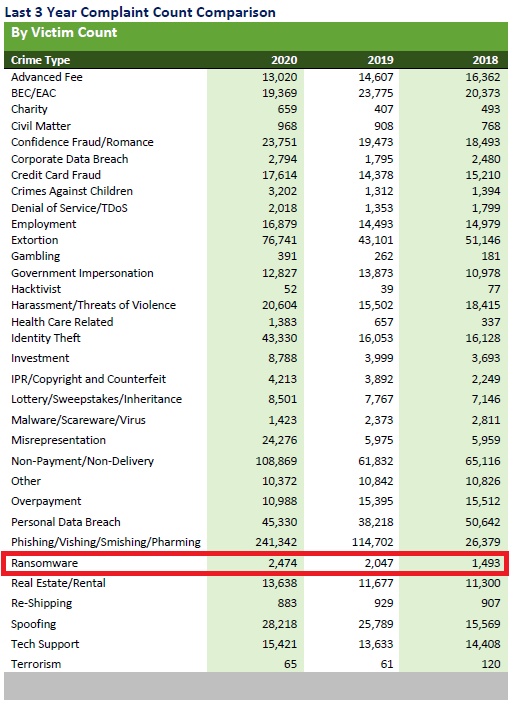
Graphic by Internet Crime Report 2020.
What is RaaS?
RaaS is a cyberattack model that replicates SaaS (Software as a Service). In other words, it is a subscription-based model in which a person asks for a “service” which turns out to be a previously designed ransomware tools "package" to attack. The "novelty" of this cybercrime is that anyone who has the money can become an attacker. Before, the number of ransomware attackers was limited to people who knew how to enter a victim’s cybernetic infrastructure and encrypt its information. Now, anyone who has the money and intentions to commit such a crime could hire that service.
How does it work?
First, cybercriminals write the ransomware code; then, the person or company involved buys (or rents) that code to execute their misdeeds. If they prefer, they can subscribe monthly or at a one-time fee. The purchased package includes a detailed step-by-step guide explaining how the program should be executed. In some cases, criminal developers add a real-time dashboard that shows what is going on with the victim.
To "sell" their service, criminals must appeal to the credibility they inspire in their potential customers. Thus, reputation becomes a key element within this model of criminality. Once the ransomware package is purchased, the next thing to do is to get the victim to download the program. For this purpose, they use well-known techniques such as phishing or smishing. From here, the procedure continues as in any other ransomware attack. Another difference appears in the distribution of the decryption data payment, which is usually made in cryptocurrencies because they are untraceable. Once the payment is made, a money launderer distributes it both to the person who bought/rented the ransomware package and to its developer.
Here we can see a workflow diagram that shows how the operation works:
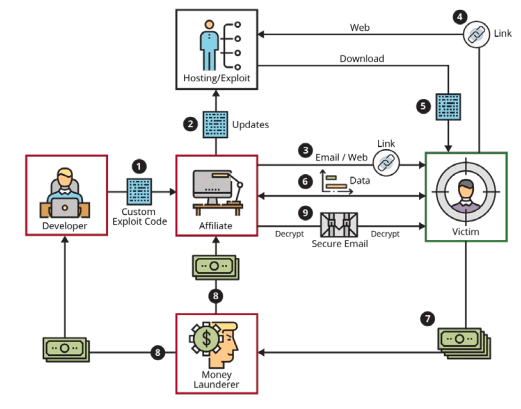
Diagram by Carnegie Mellon University.
We must highlight, together with the diagram’s authors, that in practice affiliates do not choose only one developer. In the same way, they do not usually choose a single victim, but target many at the same time.
What’s up with RaaS?
Five years ago, Stampado became popular as a RaaS because their developers asked $39 for their ransomware lifetime license package. Something super cheap considering that in 2016 subscriptions were “typically [sold] for hundreds of dollars.” The person who hired the RaaS paid $39, but demanded averagely $722. Outstandingly, in 2020 the average payment requested was $111,605. which represented an increase higher than 7,700%. However, the ransom amount varies depending on the type of ransomware that is at stake. Currently, a "cheap" payment can be $12K while an expensive one can be $1,339,878 (see image below). In total, ransomware attacks represented more than $29M in losses during 2020, only in the United States. The amount is certainly much higher because, in ransomware, data is not the only thing compromised, but also equipment, time and money paid to third-party remediation services. Besides, many companies do not report attacks received to the FBI.
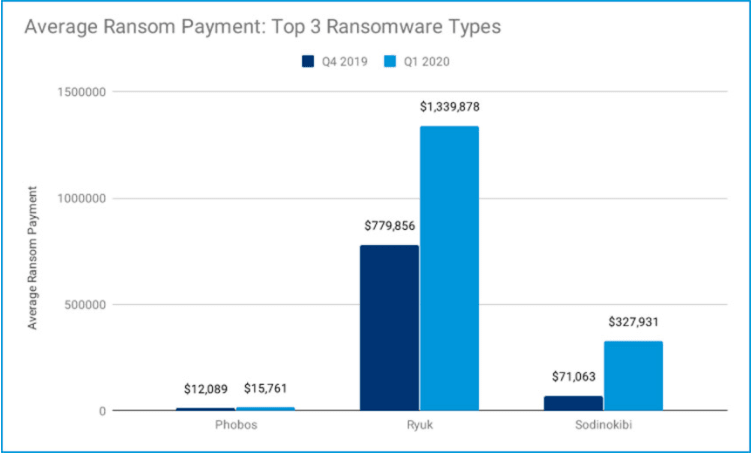
Graphic by Coveware.
One of the most recent and famous ransomware cases in the USA was the Colonial Pipeline one. This american company paid the ransom asked by the criminal gang DarkSide, which was nearly $5M. The University of California had another famous case: they paid more than a million dollars to the Netwalker ransomware gang. Outside America, the Conti attack was also famous: they asked Irish authorities $20M to free their healthcare data system. On occasions when victims refuse to pay, criminals publish their data on the Dark Web. This happened to Lady Gaga and Donald Trump last year. However, some requirements overpass the payment capacity of their victims. Such was the case with REvil ransomware, which asked $42M to Allen Grubman, the entertainment superstars lawyer (he had clients such as Bruce Springsteen, Elton John, Lady Gaga and U2). All the above means that by adopting the SaaS model, criminals get more profitable. The proof is in the pudding: the GandCrab gang, one of the most famous RaaS, announced that after a year and a half of operations their clients' profits were $2B only in ransom payments. From this, GrandCrab earned more than $150M. As we already pointed out, this model benefits criminal developers and non-developers. Now anyone could perpetrate this type of cyberattack. Finally, developers do not take risks as before, because they are no longer directly exposed to the authorities. Those who end up perpetrating the main crime are third parties.
We hope you have enjoyed this post, and we look forward to hearing from you. Contact us!
Table of contents
Share
Recommended blog posts
You might be interested in the following related posts.











