| 4 min read
Table of contents
You just won a car! Claim it here! Probably it is not the first time you’ve received this type of SMS on your phone. We probably shouldn’t have to remind you that if you receive something like this, you’d better not open it! Don’t click on any link! IT’S A SCAM! Fly, you fool! Fly! Your financial well-being depends on that. Don’t give away your money so easily to those who try to seize your keys, credentials, and personal information.
Smishing is how this type of scam is called. It represents (along with phishing, vishing, and pharming) $54M in losses just in the United States (as shown in the FBI Internet Crime Report 2020; see Figure 1. Also, click here to know more about what’s in the FBI’s 2020 Report). This is quite frustrating! It is so much money and it is so easy to avoid being victims of this type of scam. To keep criminals from robbing you like this, you must know the modus operandi of such scams. As the famous writer Frank Herbert said: Knowing where the trap is – that’s the first step in evading it.
Let’s start with the name smishing. Since it is a type of scam that occurs through the Short Message Service (SMS) of our mobiles by adapting the phishing scam method, it is known as the blend-word smishing (SMS+phishing). It is a type of cyberattack that tricks victims into sharing valuable information, installing malware, or giving away money (click here for more info). This scam has widely spread in various parts of the world. In March of this year, smishing generated £20-30M losses to the Newham’s (UK) largest banks. Last year, the Bank of Ireland also had to "reimburse a total of about €800K to as many as 300 customers who have fallen victim to a text «smishing» scam.” But how could anyone steal information, money or install a malicious program via a supposedly harmless text message?

Figure 1. 2020 Crime Types
How does smishing work?
Smishing always operates on the same principle: to be a fraudulent message that motivates the victim to provide information or click a link. In this way, we could classify this fraud into three categories:

Figure 2. Victims
-
Revealing credentials
Here, criminals expect victims to provide information about their usernames or passwords from certain online accounts. To do so, criminals send victims a message that deceives them by saying that one of their accounts has been blocked (or will be soon). To avoid this situation, victims "must click on here" and open a link that drives to a facade platform that has fields that must be fulfilled with account details. But instead of logging in or rescuing the victim’s account, what they just did was give scammers what they needed to hack them. Sadly, bank smishing is one of the most lucrative and common types of cyberattacks. Today scammers have taken advantage of the COVID-19 pandemic and pose as health system organizations to deceive people. They ask potential victims to provide data for some “medical exams” or to be vaccinated. According to the FBI report, smishing (along with phishing, vishing, and pharming) was the type of cybercrime with the highest number of people affected during 2020 in the United States (see Figure 2). It represented an increase of 110% from 2019 (see Figure 3). For example, the Federal Communication Commission (FCC) revealed that $30K were being falsely offered as a COVID-19 relief. Something similar happened in South Korea where the Ministry of Science and ICT revealed in February 2020 that "9,688 smishing texts had been sent that used false information on the novel coronavirus."
-
Downloading malware
In smishing, victims and not scammers do the dirty work. This type of scam seeks victims to click on a link to download malicious software on their phones. Once inside, they’ll be able to access the victim’s location, credit card data, or information from other apps. This category is one of the most dangerous since nowadays we tend to synchronize all kinds of accounts, contacts, credit information, and account credentials on our phones.
-
Sending money to someone
Poor friend of yours! He crashed into a terrible car accident and got lost in the middle of nowhere. There no emergency service will rescue him. Will you be the good charitable soul who’s going to make him a transaction to get him out of that mess?
This smishing category could be the most infamous one because it plays with people’s generosity. In some versions, scammers don’t play the victim, but some altruistic religious or a NGO member. Anyway, the result is the same: poor dimwits victims with a defrauded heart and great tricksters criminals with overflowing joy. If these three modalities already sounded familiar to you: congratulations! You’re one step further from being ripped off. You’re within the very small percentage of people who know what smishing is. A recent 3,500 workers survey from seven countries (the United States, Australia, France, Germany, Japan, Spain, and the United Kingdom) showed that only 30% of respondents knew what smishing was. Almost a half recognized that they didn’t know what that was.
Now that you know, how can you avoid it?
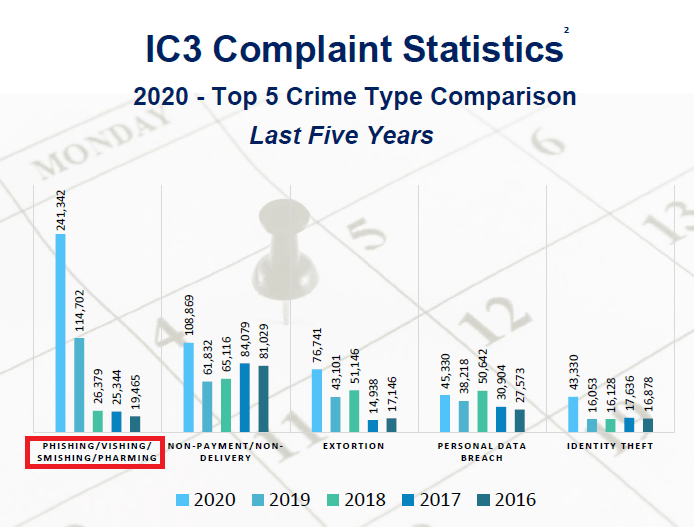
Figure 3. Top 5 Crime Comparison
Tips to avoid smishing
The first and most important one is do not open any SMS from a number you don’t know. If you think it may be real, make sure to get in touch through official communication channels (bank, health insurance, etc.). Verify the information sent to you, but NEVER CLICK on the link provided!
The second piece of advice is to always keep in mind three aspects related to bank actions:
-
Banks will never ask you for personal data by SMS.
-
Banks will never request credit card information by SMS.
-
Banks will never ask you to click on unknown website links.
Lastly: Never think you’re exempt from being a victim! You must be very careful as scammers are increasingly refining their methods. In the scammer world, this type of smishing has become one of the favorites for several reasons. People often receive lots of SPAM in their mail, which causes many of unopened emails. Thus phishing is becoming less and less popular. In comparison, we are less aware of scams via SMS, so we interact more easily. For us, our phones are very personal and reliable, contrary to emails that we are more cautious about. Unlike computers, phones generally do not have firewalls or antiviruses to hinder such scams.
If you want to know more about how to protect yourself from cyberattacks, we invite you to review our page.
At Fluid Attacks we are specialized in cybersecurity through pentesting, ethical hacking and red teaming. For more information, don’t hesitate to contact us!
Table of contents
Share
Recommended blog posts
You might be interested in the following related posts.











