| 7 min read
The zero trust philosophy is a great approach to cybersecurity. It has seen exponential growth over the past years due to the principles and components it relies on. One of those components is the Zero Trust Network Access (ZTNA), which is zero trust applied to networks. ZTNA serves as an alternative means of securing an organization's network by departing from the blind trust models so commonly used in legacy models like the castle-and-moat, thus creating a more secure and adaptable posture that supports efforts to battle cybercrime.
The castle-and-moat model uses private networks, like VPNs, to manage remote access. They act as tunnels for authorized users outside the network, and once inside, users get to access the resources they need to perform their tasks. However, VPNs have their limitations and severe drawbacks when it comes to security, which we’ll explore in this blog. ZTNA, on the other hand, makes access to company resources much safer, strengthening its security posture.
Zero Trust Network Access
ZTNA is an IT solution that focuses on access controls and user/device authentication to provide secure and granular access to resources. ZTNA primarily deals with securing access to resources like applications, systems, services and data within a network, from any remote location and from any device. This solution is established to deny access unless explicitly allowed. ZTNA solutions typically use features such as app microsegmentation, identity-based access controls, access policy configuration and encrypted tunnels to secure access to applications and data, regardless of the network user's location.
How does ZTNA work?
This is how Zero Trust Network Access typically works:
-
When a user or device attempts to access a network resource, the ZTNA solution verifies their identity via authentication mechanisms such as usernames/passwords, multi-factor authentication (MFA) or biometric authentication.
-
The ZTNA solution first evaluates the security posture of the user's endpoint, which may include checking it for patches, updates and upgrades.
-
Afterward, the ZTNA solution enforces access policies based on contextualized information such as user roles, device type, sensitivity of the requested resource and time of access to provide access to a specific application or system.
-
Once a user or device is authenticated and authorized, the ZTNA solution creates a safe, encrypted tunnel between it and the resource it’s trying to access. This ensures that the data transmitted is protected from interception or tampering.
Benefits of ZTNA
In today’s cloud-based world, ZTNA offers several advantages to companies looking for a more secure approach to access management. Here are some of the key benefits:
-
User/device identity authentication such as knowledge-based authentication (personal credentials), biometric identification and multi-factor authentication. All instrumental to keeping resources secure.
-
ZTNA enables safe remote access from any place or device as long as verification is passed. This flexibility is ideal given the growing number of remote workers.
-
The security posture of a company is improved by following the zero trust philosophy of “never trust, always verify.” It helps organizations reduce the attack surface and mitigate the risk of internal and external breaches or attacks.
-
Cloud-based ZTNA solutions are easy to deploy and reduce the risk of accidental access grants.
-
ZTNA offers flexibility in case a user/device needs new authorizations.
-
ZTNA improves traceability and visibility into user/device activity and access attempts through traffic logs, which is valuable information for security monitoring and auditing.
-
ZTNA offers more granular control over network access compared to VPNs (virtual private networks) or VDIs (virtual desktop infrastructures). This granular approach minimizes the risk of unauthorized access.
-
ZTNA allows for device posture validation (OS, firewall, antivirus, source IP, disk encryption), contributing to the overall cybersecurity strategy.
ZTNA vs. VPN
A VPN acts like a tunnel between two networks or endpoints across an intermediate network (e.g., the internet). VPNs are mostly used by remote workers who need access to their company’s network in order to perform their duties. Once users have provided their credentials, they can move through the network as they please and are trusted with access to the company’s resources. Advantages of VPNs include remote access flexibility, data encryption and simple implementation. Every organization’s needs and budgets are different, but there are things to consider when trusting VPNs.
VPNs offer competent data security, but their nature of inherent trust makes them an easy target for hackers, since getting credentials through social engineering or brute force has become child’s play for them. Data travels encrypted through a tunnel, which protects the data, but VPNs don’t ensure that endpoints or networks connected by the tunnel are secure. Also, encrypting and routing data through VPN servers can slow down internet traffic. Uptime is not always assured; hardware failure or software bugs can interfere with productivity and create disruptions. VPNs are generally the less expensive solution for remote access; however, add-ons like extra security solutions, licensing and maintenance increase the total cost of ownership.
What’s the difference between ZTNA and VPN?
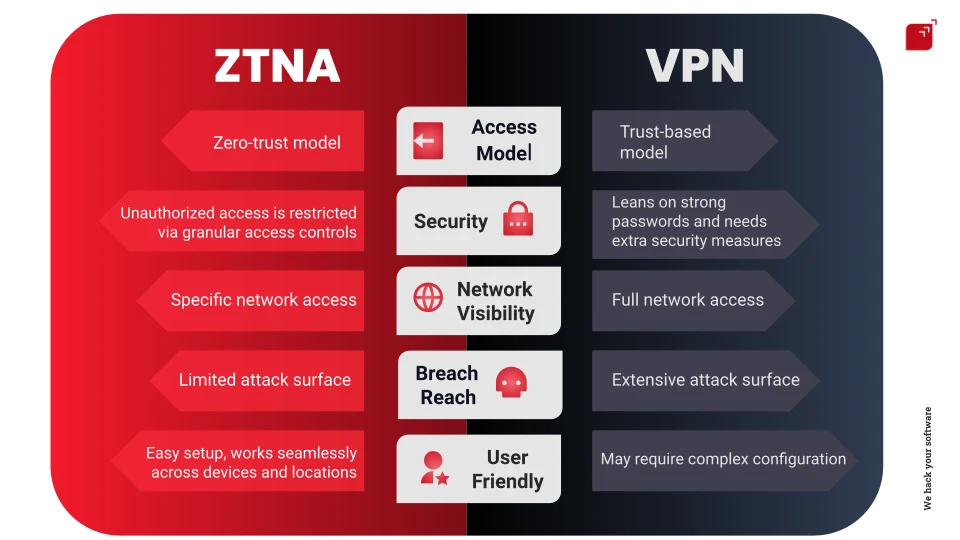
ZTNA vs. VPN
Solutions for secure network access include both ZTNA and VPN. Although they support remote access, ZTNA has a few significant advantages over VPN, particularly in terms of establishing trust and access control. VPNs don’t innately check the endpoint security posture, extra software has to be installed and constantly updated. ZTNA performs an endpoint-to-endpoint verification as its initial step, and it won't establish a connection unless the endpoint security assessment has passed.
While VPNs rely on the user’s good password and resource management practices, ZTNA’s zero trust approach of granular access enables a company to control the resources a user can view and use. In cases where segregated environments need to be accessed, another VPN controller has to be set up and managed separately. Not only is it less pragmatic, but VPNs can also be a security risk as they expose more systems to potential threats. On the other hand, ZTNA solutions provide a more user-centric and secure approach by limiting access to only authorized applications and offering granular access, which reduces the probability of attackers moving laterally.
Monitoring traffic or user activity for auditing purposes is not possible with VPNs, making it useless if a company wants to track who or what is connecting to its resources. Most ZTNA providers are equipped with a sort of agent manager that provides information like the user’s ID, authentication method, endpoint status, GPS location, and much more.
After successful authentication, traditional VPNs grant access to entire networks. This allows all resources to be used and, in case of an attack, provides a large attack surface. The zero trust model advocates the “least privilege” principle, which, if correctly applied, limits the attack surface if a breach occurs. With VPNs, users may need to install software, configure settings and troubleshoot connection issues, all of which require an IT team to be on call. On the other hand, after initial set-ups, ZTNA solutions are often cloud-based, needing minimal configuration, no matter the location or the device. Workflow is streamlined, and potential disruptions are reduced.
From VPN to ZTNA
Overall, ZTNA is often seen as the more modern and secure solution for remote access, no matter the environment (cloud or on-premises). VPNs are still a viable option for some instances, especially for small organizations with simple network needs, but as stated previously, they need extra protection layers both inside and outside the network perimeter. Companies that have realized security is non-negotiable are migrating to ZTNA. And, in all honesty, making the switch is not an easy undertaking, but once it’s been done, it will all pay off.
Switching from VPN to ZTNA requires a comprehensive and careful phased migration plan, taking into account that testing should be done before deployment, along with considerations for budget availability and clear user training to address potential concerns. Security policies must be revised and, for the most part, rewritten in order to reflect the zero trust approach. In the case where ZTNA will integrate with existing infrastructures, the chosen ZTNA provider should come up with a road map to make a smooth unification. Monitoring should include system performance, scalability needs and user activity after deployment to identify and address issues that arise.
There are some misconceptions that VPN users might have about zero trust or ZTNA, so let’s discuss them.
-
“You have to move to the cloud to implement zero trust.” Not true. ZTNA solutions can function for both on-premises and cloud access without compromising performance.
-
“ZTNA is only a remote access solution.” Not true. ZTNA is mainly used in remote work access, but zero trust solves a security problem (accessing resources with proper authentication and authorization) that all companies have, including in-person workplaces.
-
“Switching to ZTNA requires expensive infrastructure upgrades.” Not true. Many ZTNA solutions are designed to work with a company’s existing infrastructure, which reduces the need for upgrades. This makes ZTNA a cost-effective solution in the long run.
-
“Zero trust is a cure-all solution.” Not true. While zero trust and ZTNA have the potential and ability to enhance a security posture, they’re part of a bigger cybersecurity strategy that works with other methodologies and tools to keep a company secure.
Fluid Attacks’ usage of ZTNA
Data breaches, ransomware attacks and other cybersecurity incidents tend to be the result of improper security practices. ZTNA, in the philosophy of zero trust, emphasizes the need and value of a conscientious cybersecurity strategy. For Fluid Attacks, ZTNA is essential in order to perform the Continuous Hacking solution. We use Cloudflare's ZTNAs as secure tunnels to connect to our clients' networks, safeguarding our interaction, which is one of our biggest priorities as a company.
When connecting through our ZTNA, our clients benefit from:
- Leverage the principle of least privilege establishing which resources we’ll be able to access within their network.
- Our platform provides tunnel navigation traceability logs that can be used for network audits.
- We require comprehensive identity authentication that adheres to strong password policies and multi-factor authentication processes.
- The connected devices go through a thorough verification process that includes checking for latest operating system versions, updates and patches.
- We also enforce the need for an enabled firewall and encrypted hard drive.
We don't request our clients stop using their remote access methods. Only when connecting with us, do we want them to use our established ZTNA solution. We adhere to the zero trust philosophy of “never trust, always verify” and we put it into practice when our clients provide us access to their code or applications. We know how crucial a robust security model is, and we want you to benefit from it, so contact us now.
Recommended blog posts
You might be interested in the following related posts.











