| 5 min read
Ransomware, ransomware, ransomware; everyone is talking about it. Thinking about being a victim of ransomware surely scares many of us. Nevertheless, despite all the dissemination about it, many people may not be, or irrationally may not want to be, sufficiently aware of it. That’s why we continue to publish information related to this type of attack. Also, because it is a phenomenon that continues to evolve, and new groups of criminals with different forms of malware and strategies keep sprouting up and shooting at new targets. Today it’s time for LockBit, the ransomware behind which there is a gang that would like to hire some of your employees. Let’s see what it’s all about.
What is LockBit, and what does it do?
Two years ago, the data encryption malware LockBit began operating, which later became part of the Ransomware as a Service (RaaS) model —something we have already referred to in a previous post. Among Lockbit’s outstanding attributes are its abilities to self-propagate and encrypt large and valuable enterprise IT systems in a short time to avoid detection. As Ilascu for Bleeping Computer once said, "LockBit attacks leave few traces for forensic analysis as the malware loads into the system memory, with logs and supporting files removed upon execution."
LockBit is launched by attackers through a PowerShell script, usually after compromising a network, for example, by brute force or phishing (or at one of your employees' own will). This malicious software disables the security and information recovery programs as a preliminary step in an independent way. Once the network is vulnerable, LockBit automatically spreads easily across different devices. From there, in its operation as ransomware, it starts encrypting system files. And, as shared in Kaspersky, "Victims can only unlock their systems via a custom key created by LockBit’s proprietary decryption tool." LockBit changes the names of the file extensions on the target device to ".abcd" and creates a text file in each affected folder, with instructions for the victim, called "Restore-My-Files.txt" (see image below).

Restore-My-Files.txt screenshot (source: howtoremove.guide).
The victim then has at her disposal a Tor link through which she can learn more about the ransomware, even establishing direct communication with one of the LockBit operators. These conversations begin to revolve around "the ransom demand, payment deadline, method —usually in Bitcoin— and instructions on how to purchase cryptocurrency," said Osborne for Zero Day. The victim also receives the opportunity to decrypt and recover a small file as a supposed warranty that the other files can be retrieved once the payment is made. We must also note that, apart from this ".abcd" variant, we can also find the ".LockBit" extension variant and even a version in which the Tor browser (generally used for the Dark Web) is no longer required.
On the other hand, among the improvements to this malware that were reported later, we can recognize its ability to disable the security prompts that users receive when an application tries to run as administrator. LockBit now has a configuration that allows it to steal copies of data from servers. That’s data that can be made public at the whim of the attackers, especially if the victims are reluctant to respond with the requested payment. LockBit, in its 2.0 version, has "one of the fastest and most efficient encryption methods in today’s ransomware threat landscape," according to Trend Micro. Another significant change (in terms of presentation), for many people outlandish, has been the offer of millions of dollars in exchange for "corporate insiders" who help breach and encrypt the targeted companies' networks (see image below).

LockBit 2.0 wallpaper for insider recruitment (source: bleepstatic.com).
An eye-catching recent case
It is now common for ransomware payouts to reach millions of dollars; remember the case of JBS. However, according to Osborne, LockBit affiliates are currently requesting an average of around 85 thousand dollars from each victim, of which 10-30% corresponds to RaaS operators. One of the most reported cases of attack with this malware in recent days has been the hit on the Fortune 500 professional services and consulting multinational Accenture. They were listed on the leak site of the LockBit group next to a countdown timer, and the operators left a short message from a supposed insider (see image below).
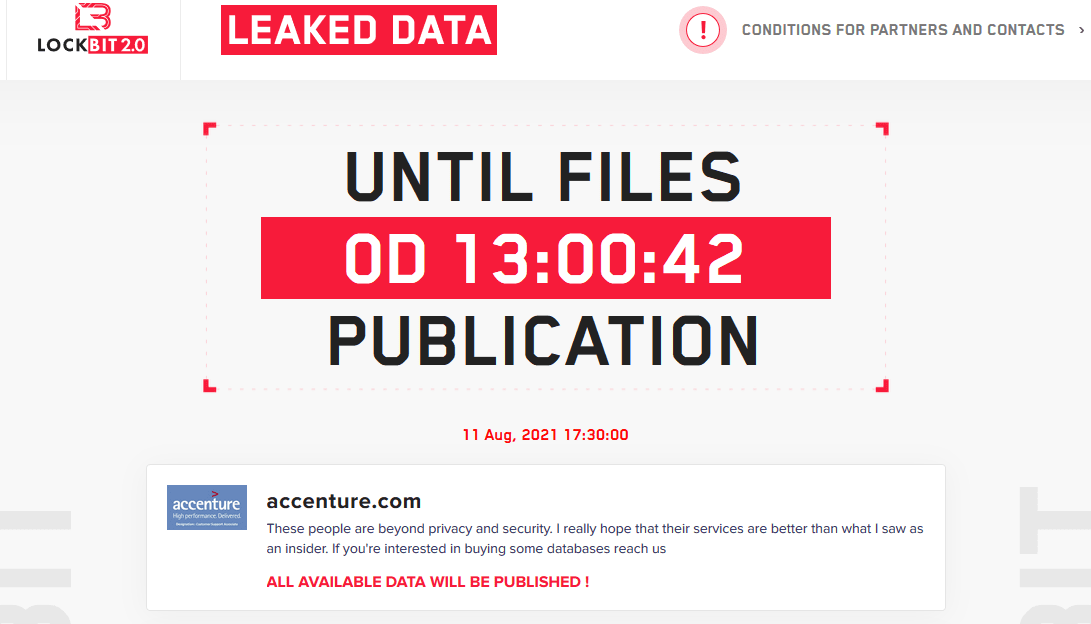
LockBit page screenshot (source: zdnet.com).
Once the timer reached zero, some of Accenture’s information would be released, and indeed it was. However, there was no sensitive information there —mainly marketing material. The company had already said that the ransomware had not affected its operations and that they had managed to restore systems from their backups. From the research firm Cyble, there was commentary that the LockBit group was demanding $50M as a ransom for a database of approximately 6TB. Do they really have all that data, and will they reveal it later? Or is it just a bluff? Has Accenture already made a payment? One thing that seems clear for now is that the attack’s aftermath will be a bad reputation for this organization, at least as far as its cybersecurity services are concerned.
For the umpteenth time, let’s question ourselves
Today, it is quite curious that most of the companies that were victims of ransomware attacks and paid the ransom (said to be around 80% within one study) have been victims a second time, perhaps even at the hands of the same criminals. How not to come to one’s senses after such a blow? Professional services and sectors such as transportation, construction, and food are among the most threatened by LockBit around the world. Within these sectors and, in fact, within all companies, cybersecurity should gain priority, primarily in terms of prevention. But we are witnessing the paltry value that messages like "don’t wait to be attacked to take action" are having. Now, in many cases, there’s no action even after impact!
Regardless of the veracity of what a man referred to as "Aleks," an alleged LockBit operator, told Cisco Talos a year ago, some of the words he conveyed could work as an additional nudge for many of us. Not a boost to criminality, of course not, but to adequate security practices. What Aleks said was that he became interested in ransomware because of its profitability but that it also allowed him to "teach" organizations about the consequences of inappropriate data protection. Therefore, it is worth asking, how sure are you that your software and systems are in optimal security conditions?
Additionally, the intentions of LockBit 2.0 are already forcing even many to ask questions perhaps not previously considered. We now enter the area of reliability of your staff. To conclude, a perfect example of such questions is the one posed by Div of Cybereason:
Can you be sure that there is nobody in your company who might consider potentially making millions of dollars by helping to launch a ransomware attack?
At Fluid Attacks, we can help you with cybersecurity from prevention. Contact us!
Recommended blog posts
You might be interested in the following related posts.











